[TSCTF-J2023]逆向工程题解
[TSCTF-J2023]逆向工程题解
前言
TSCTF-J2023 Reverse试题落实立德树人根本任务,遵循德智体美劳全面发展要求,贯彻《深化新时代CTF改革总体方案》,体现了TSCTF-J改革的方向。试卷突出逆向工程学科特点,加强基础性与关键能力考查,充分发挥逆向工程学科的选拔与引导功能。TSCTF-J2023 Reverse坚持立德树人,体现CTF文化的育人价值,突出理性思维的价值,注重计算机基础性,引导学生对CTF概念、方法更深刻的认知,在基础性、综合性、应用性、创新性等方面都进行了深入的考查。试题稳中有变,变中有新,难度设计科学。 较好地发挥了TSCTF-J的选拔功能,对萌新学习逆向知识发挥了积极的引导和促进作用。
题目在此
The_Path
不知道各位在做这道题的时候有什么想法,反正我是挺想骂街的。添加了与[2019红帽杯]easyRE一样的主动防御。本着不能只有我一个人受苦的优良品德,出了这道题。打开看见:
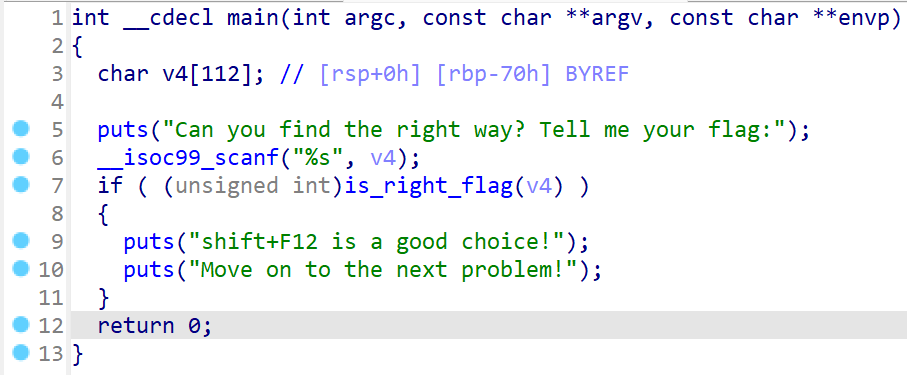
给人感官极其良好,但是稍微往左瞥一眼就会看见:
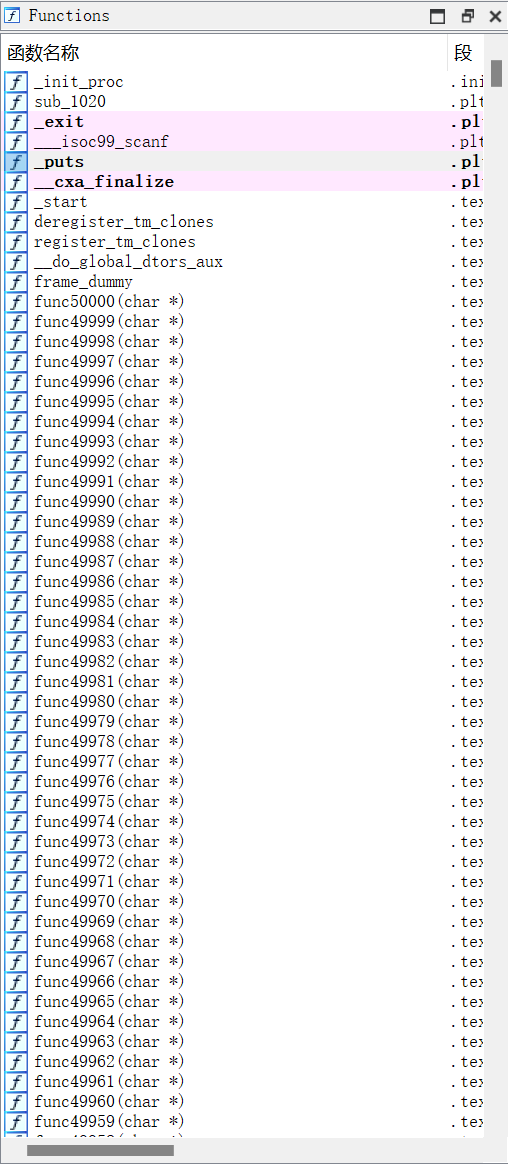
是的,我创造了50000个函数。根据提示摁下shift+F12可以根据特殊字符串找到:
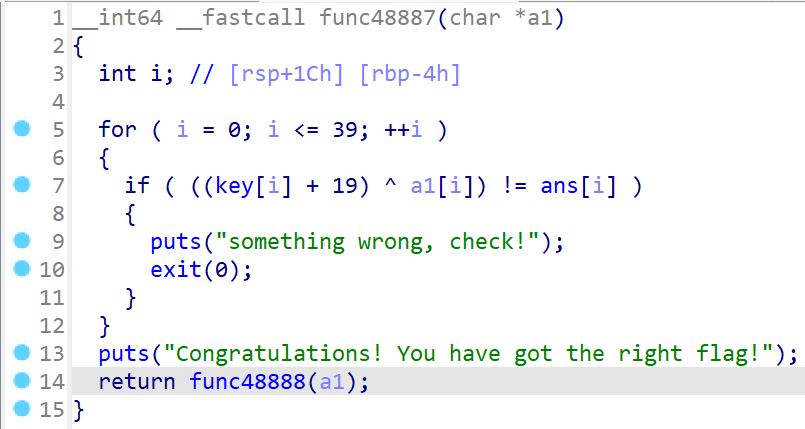
然而,解完却得到了https://bbs.kanxue.com/thread-254172.htm。 非常好,被骗了。观察数据可以发现在key和ans上面存在着enc和box两个没用到但已初始化的数组:
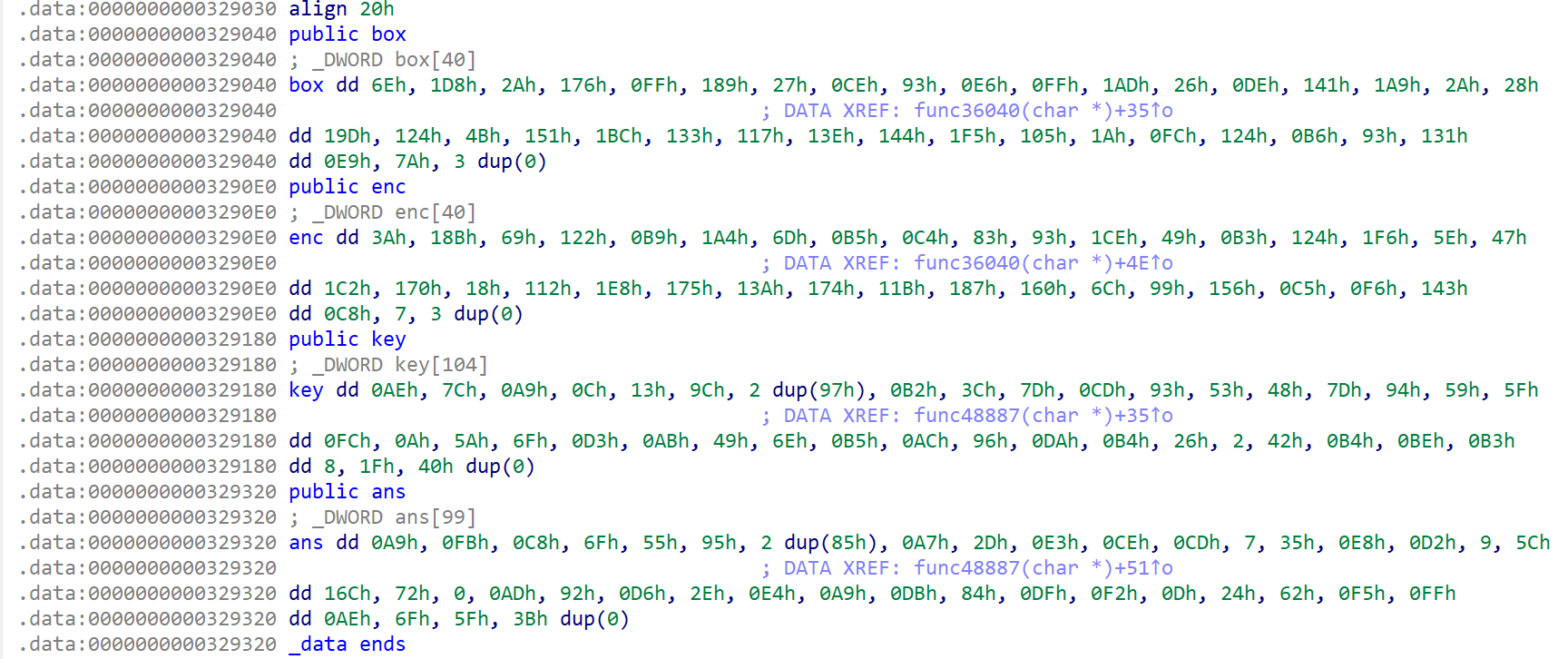
跟进可以找到真正的加密函数:
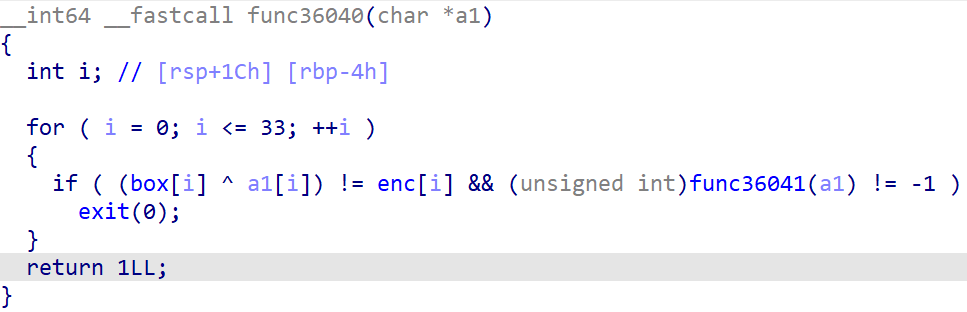
解得flag:TSCTF-J{Welcome_to_TSCTF-J_reverser!}
将文件用010editor打开可以在最后看见彩蛋:
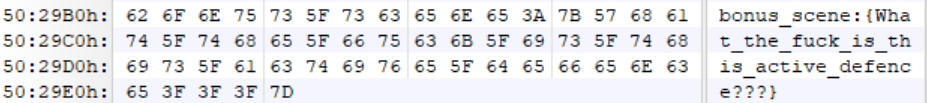
The_Encryption
这道题很繁琐,很傻逼。打开看见:
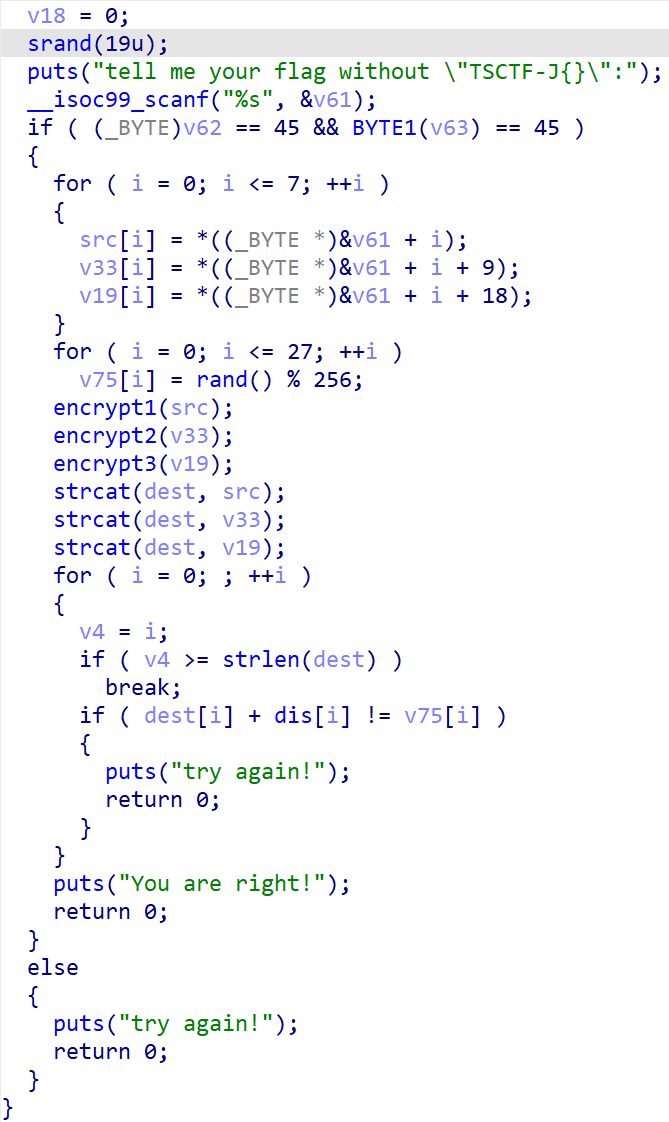
根据他们在栈上的位置可以改改名字:
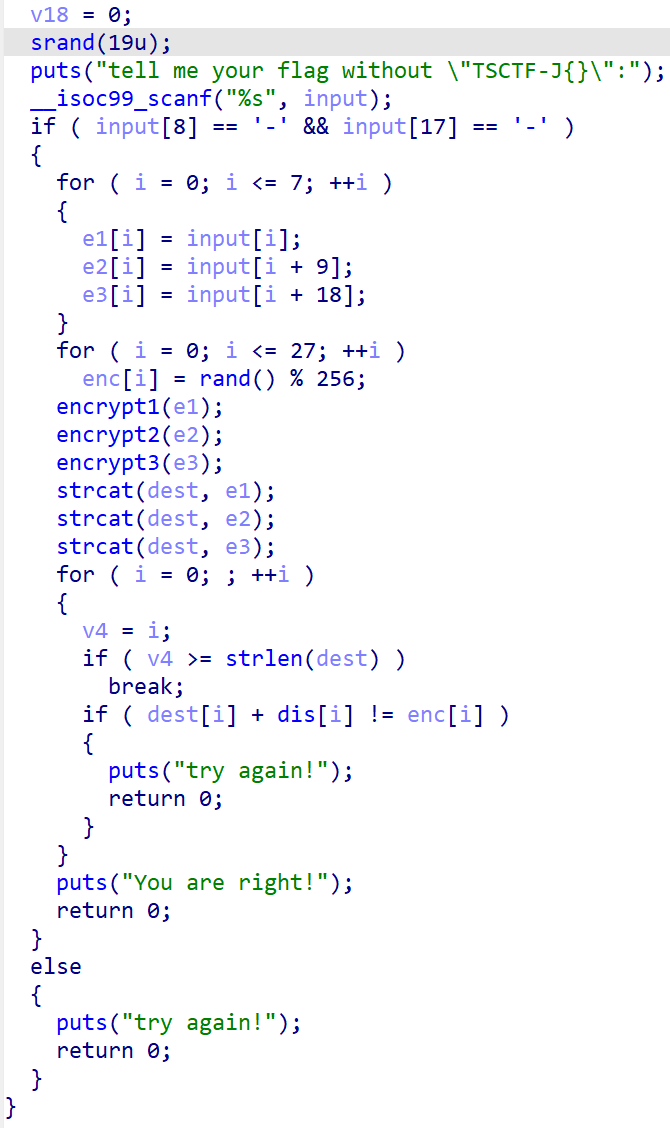
点进去可以看出encrypt1是变表的base64加密,encrypt2是TEA,encrypt3是RC4。用我们小学二年级就会的代码可以写出来:
1 |
|
得到flag:TSCTF-J{ai8v3m0z-2kf6cj1a-74bfuzx6}
想不到吧,flag是乱码,哈哈哈哈哈哈。
The_GoBang
C#逆向,逆向软件使用dnSpy。不推荐运行附件,攻击性挺强的。
在GoBang命名空间,Flag类中找到GetFlag方法:
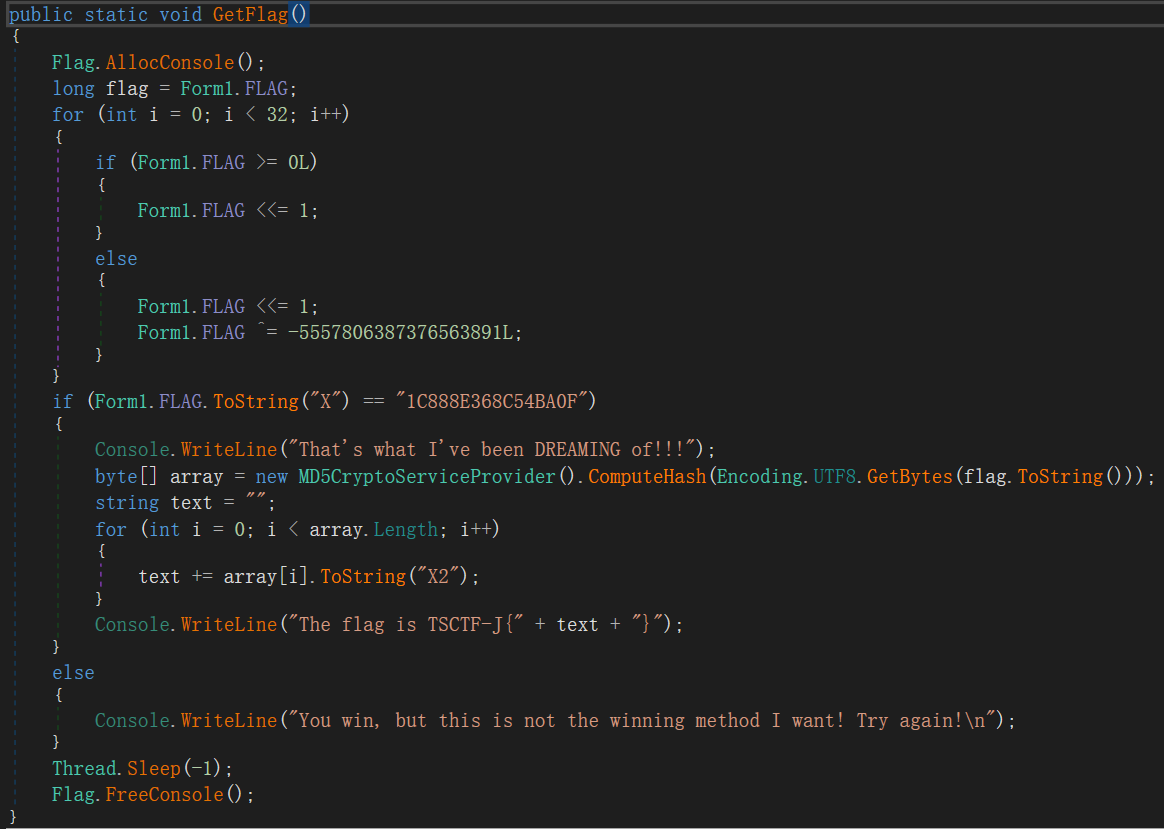
这个算法乍一看好像并不可逆,但仔细观察可以发现如果执行if块,得到的必定是偶数,如果执行else块,得到的必定是奇数。
据此可以写出代码:
1 |
|
据此可以得到7677464758678594。
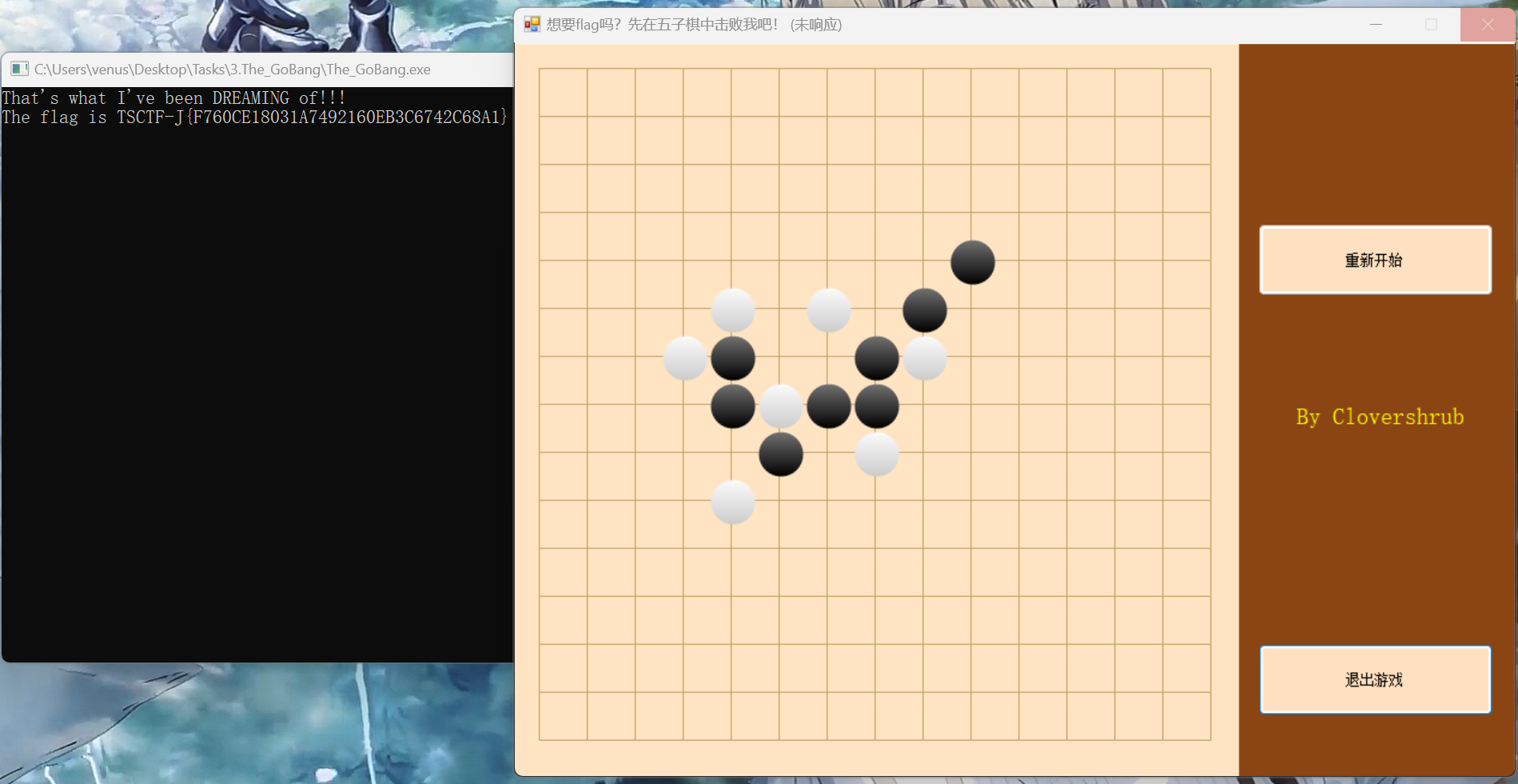
根据GoBang命名空间,Form1类panel2_MouseDown方法可以知道这串数其实是下棋的点位。
运行得到flag:TSCTF-J{F760CE18031A7492160EB3C6742C68A1}
不想运行直接MD5也是可以的。
The_Step
此题考查选手动态调试的能力。打开之后改改名字看见:
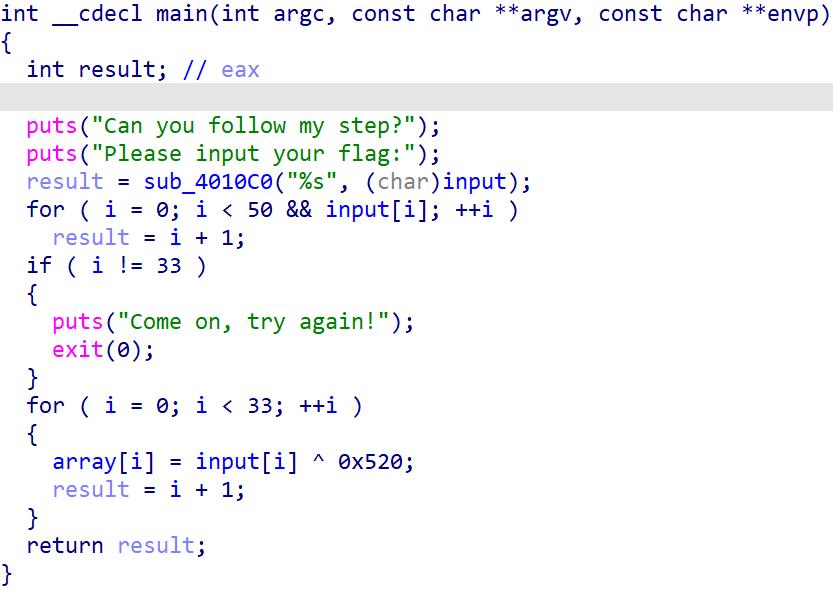
main函数戛然而止必定不对劲,选择动态调试。发现进入:
接着进行可以发现进入:
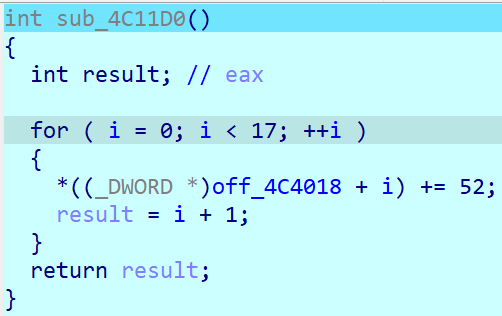
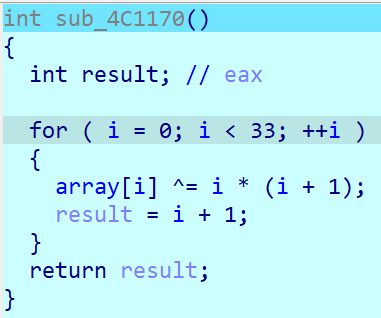
查看off_4C4018可以发现它其实是array[10]。
接着进行可以发现进入:
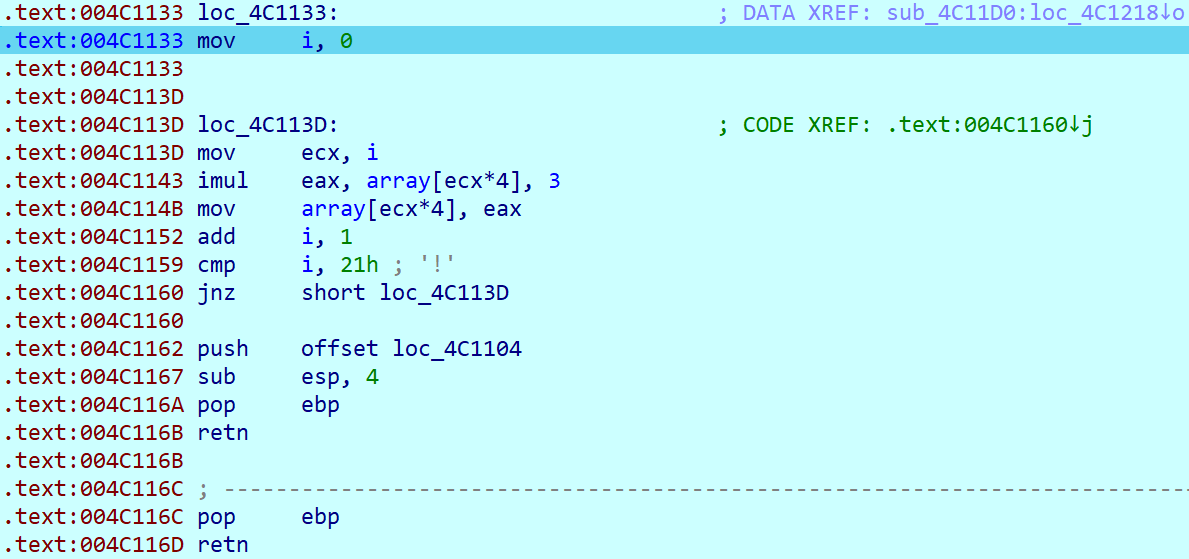
此时,要么硬读汇编,要么全选之后摁P,再摁F5,就能看见伪代码。
接着进行可以发现进入:
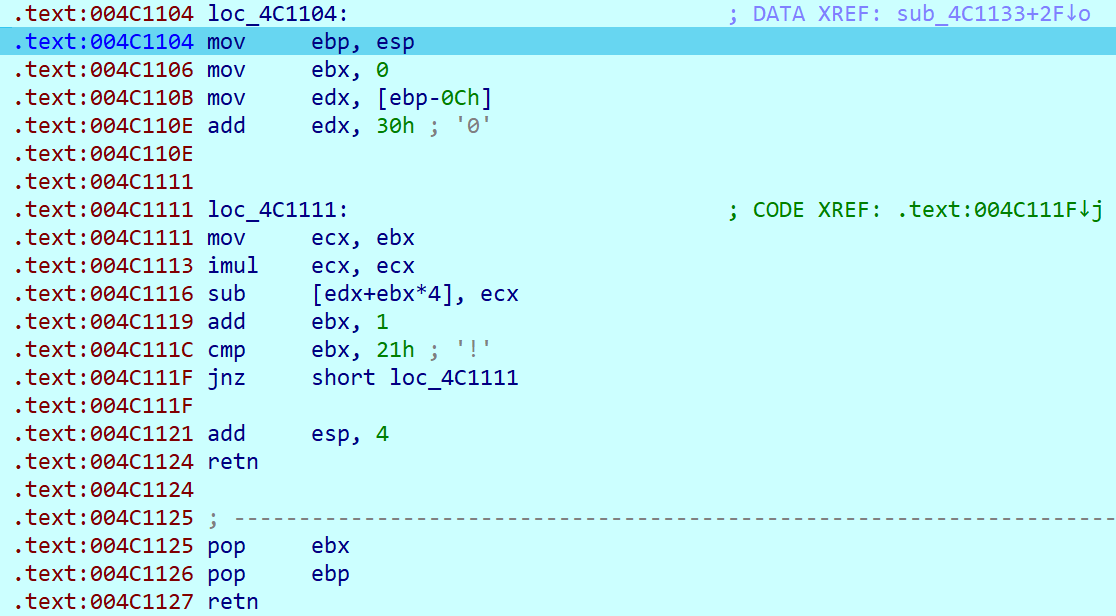
执行完4C110B的代码后将鼠标放在edx上可以发现edx其实就是array。
接着进行可以发现进入:
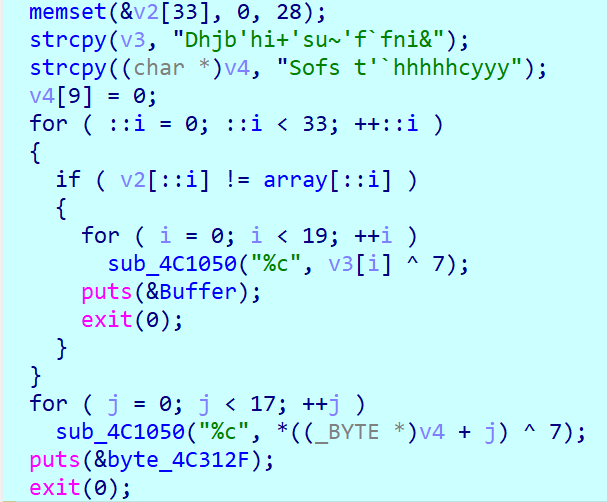
这里就是对比数据了。至此,我们可以写出代码:
1 |
|
运行得到flag:TSCTF-J{Oh_You_CAn_ReAlLY_dAnCe!}
The_Magic
TLS回调函数+SEH异常处理。
跟进线程会解出TSCTF-J{You_are_too_young_too_naive!}。同时在main和thread中下断点均断不住程序。根据提示找到TLS回调函数:
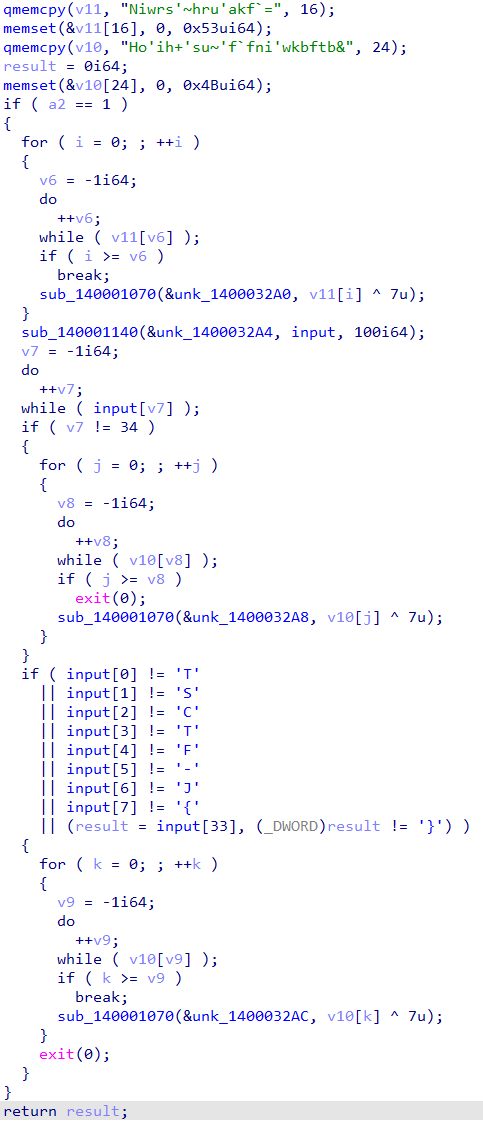
第一段是进行33位的输入。找到第二段:
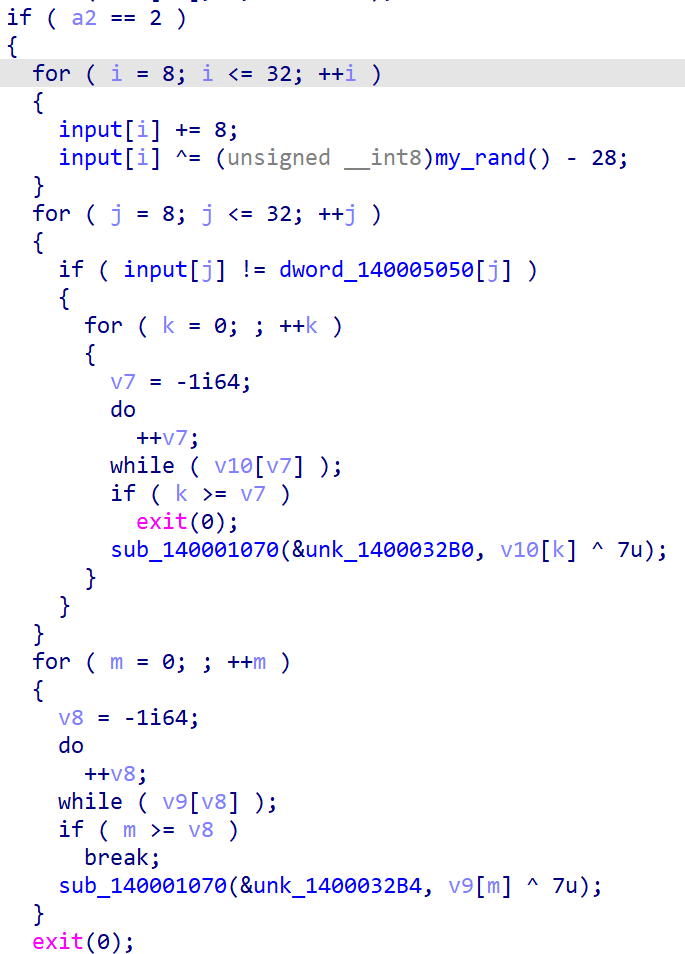
可以找到加密部分。但是如此解密会得到一串乱码。如果你尝试过动调,会发现程序在不停地报错,但是如果选择将错误反馈给程序又能继续执行。根据提示查看汇编,找到try-except块:
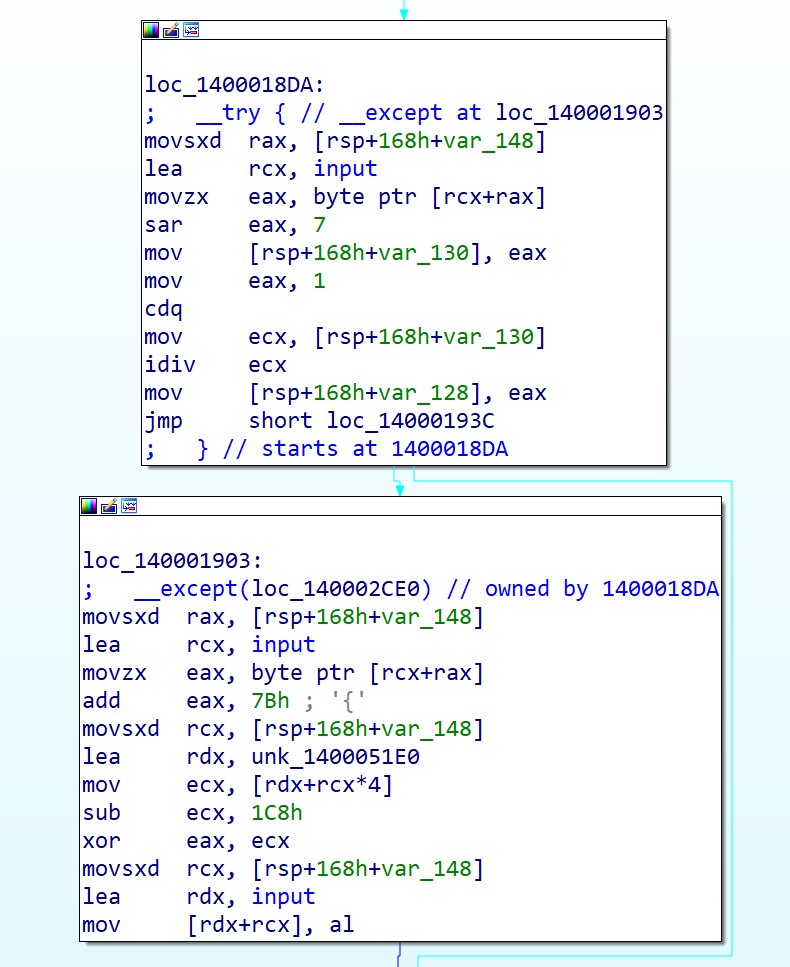
由于except块不在正常的程序执行流程当中,因此IDA会在分析伪代码的时候将其忽略。接下来可以硬读汇编或者让某一个跳转语句跳转到except块,然后再F5看伪代码。总之,可以写出脚本:
1 |
|
运行得出flag:TSCTF-J{Y0u_4r3_a_8r3at_m4g1cIan!}
The_Shell
手脱UPX壳。根据提示的这篇文章使用x64dbg手动脱壳。打开可以看见程序开头的一堆push已经被nop掉了,但我们仍然可以根据RSP的变化下断点运行,寻找大跳。
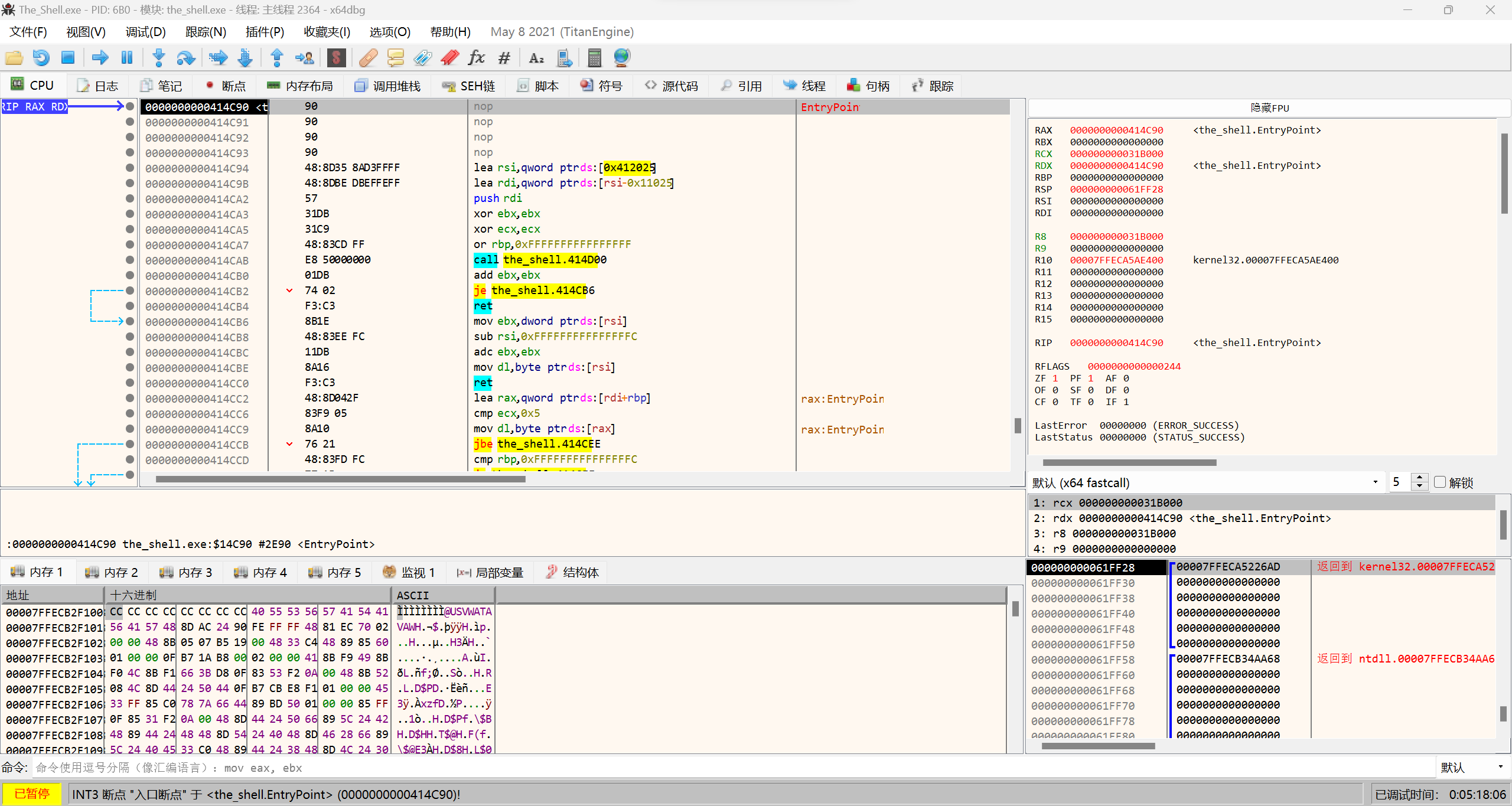
最后找到程序的OEP是0x4014E0。
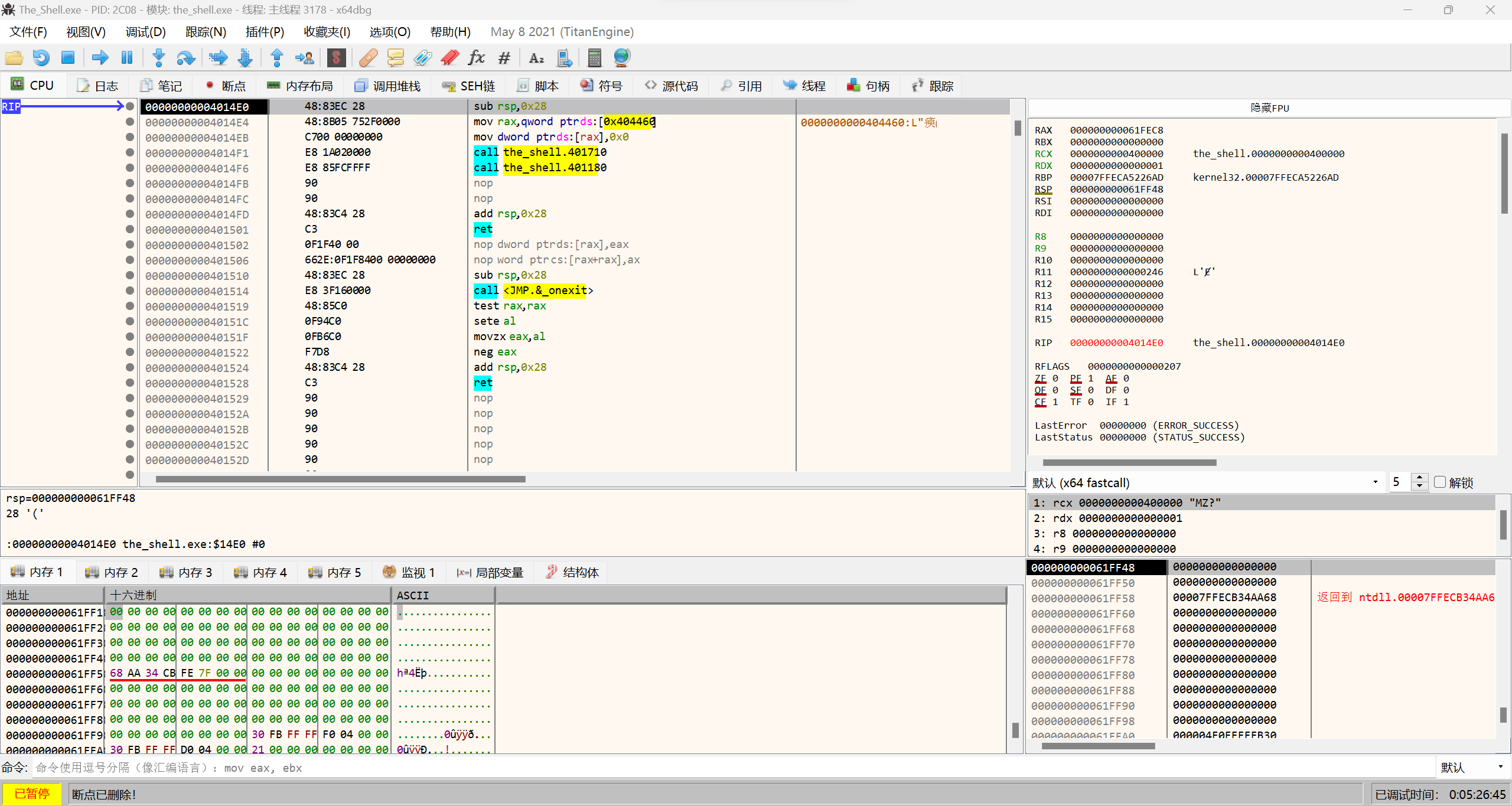
修复转储后用IDA打开可以看见:
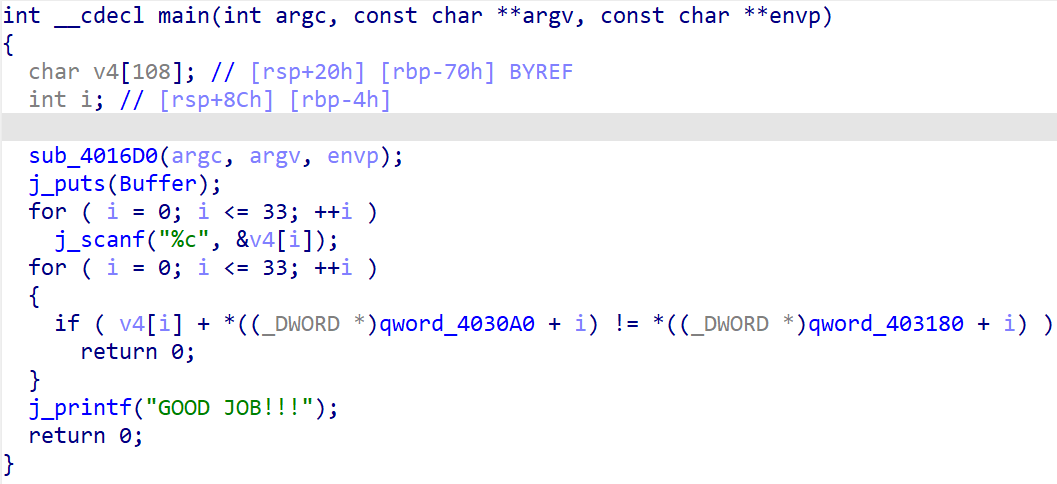
这个非常简单,可以写出脚本:
1 |
|
解得flag:TSCTF-J{Such_a_beautiful_SHELL!!!}
在查找数据时可以找到彩蛋:
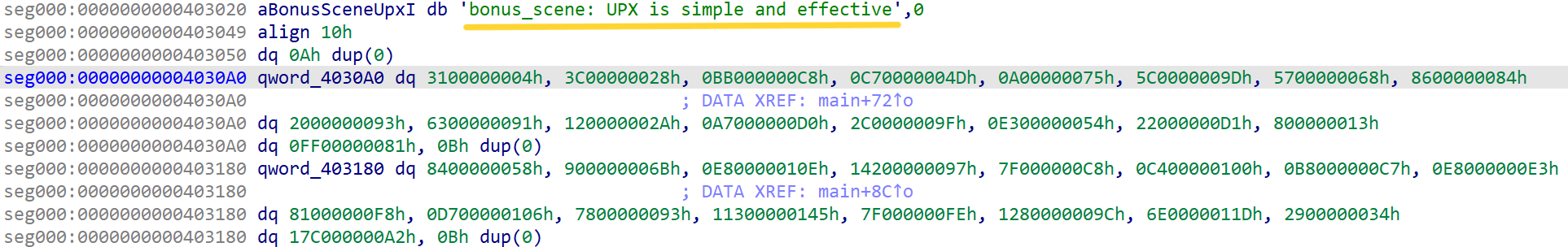
The_Art
代码自修改+花指令。
打开后发现无法F5,且汇编指令只能看懂这些:
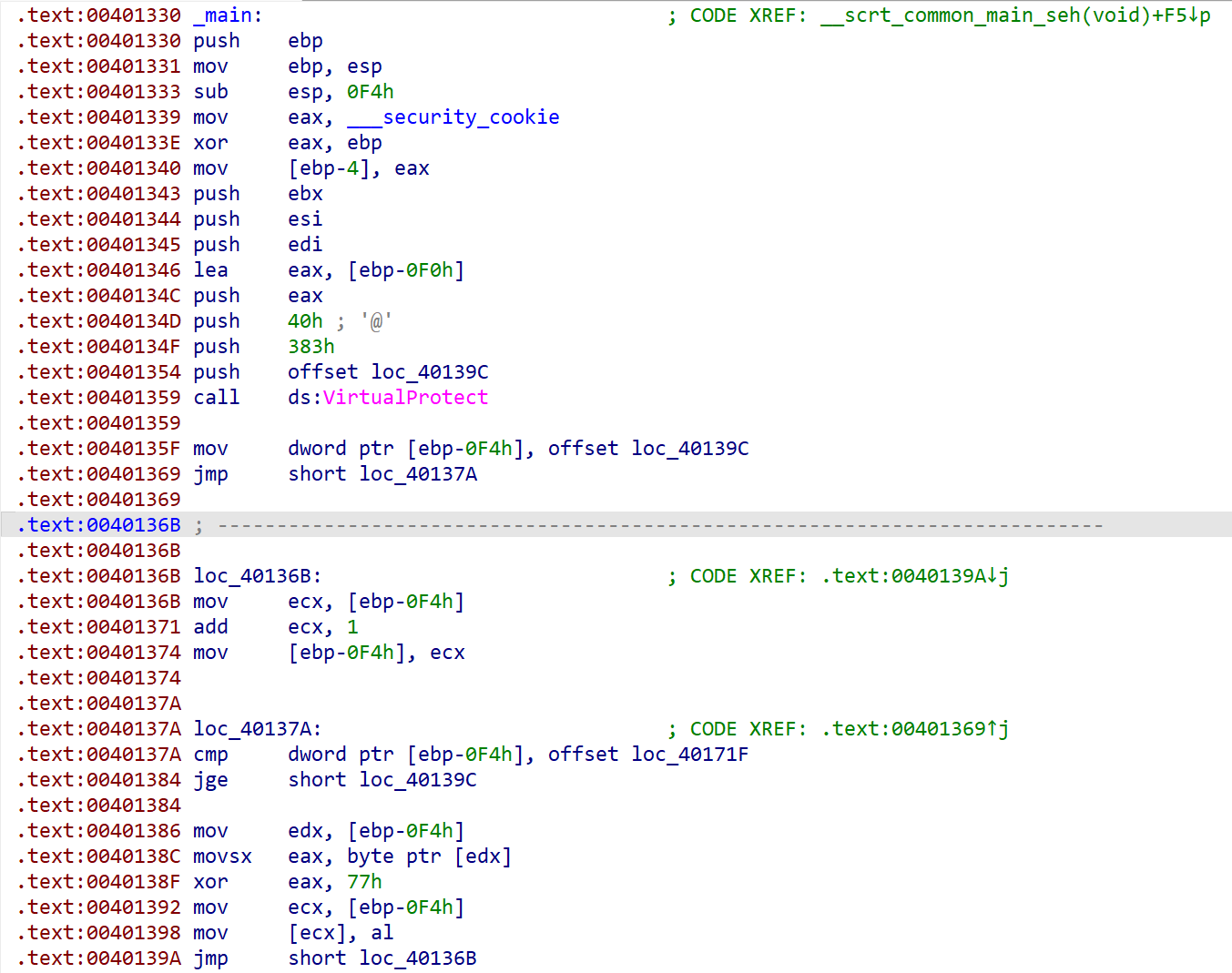
硬读汇编可知程序将接下来的代码段每一位异或了0x77。写出如下IDC脚本:
1 |
|
然而,依旧无法F5,查看汇编可以找到:
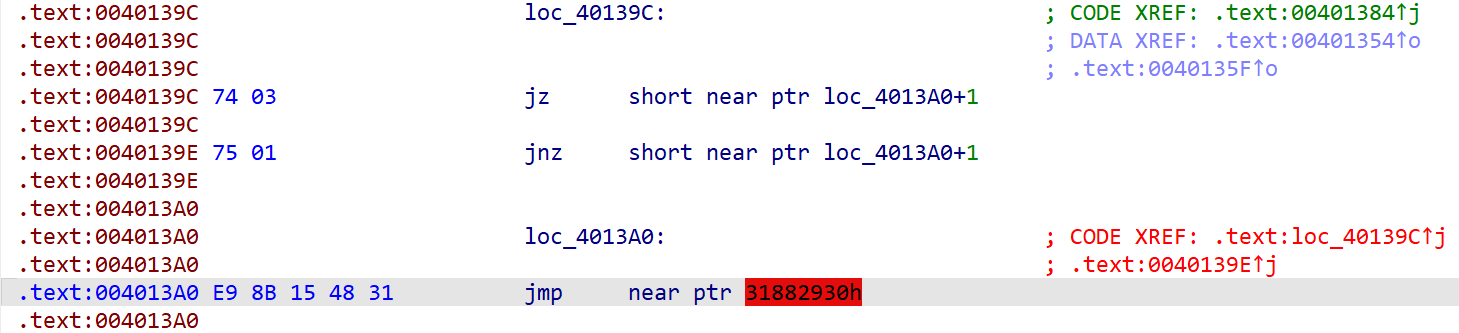
将E9改为90后终于可以F5了,可以看到:
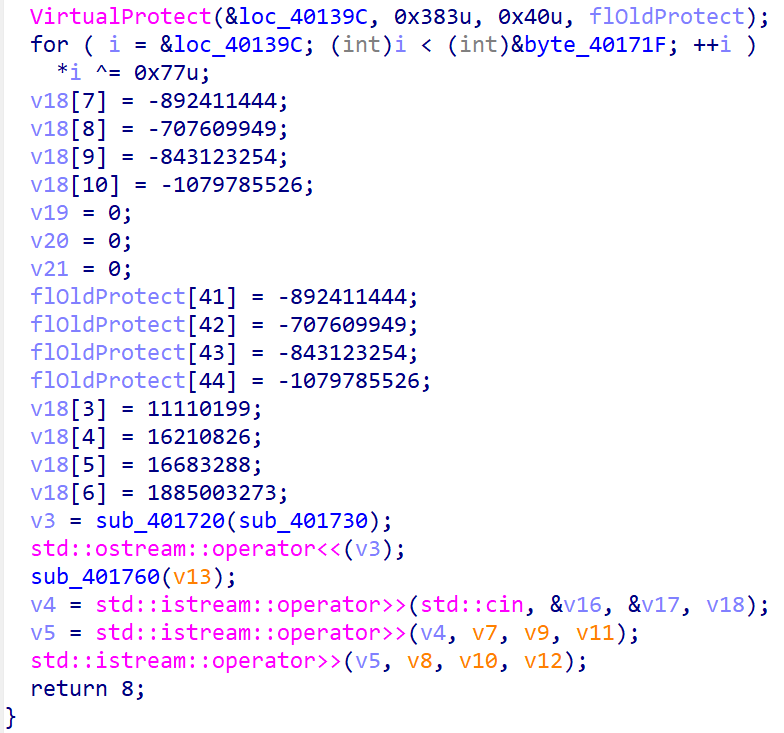
很明显,这段代码并不完整,继续查看汇编可以找到:
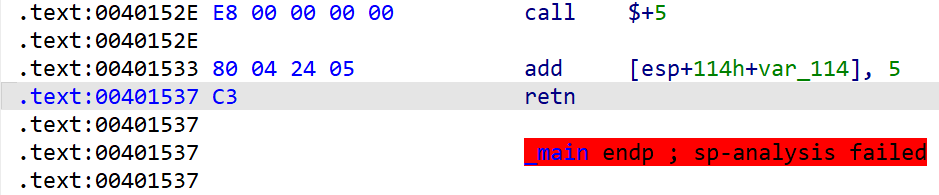
将C3改为90后就可以得到最终的伪代码:
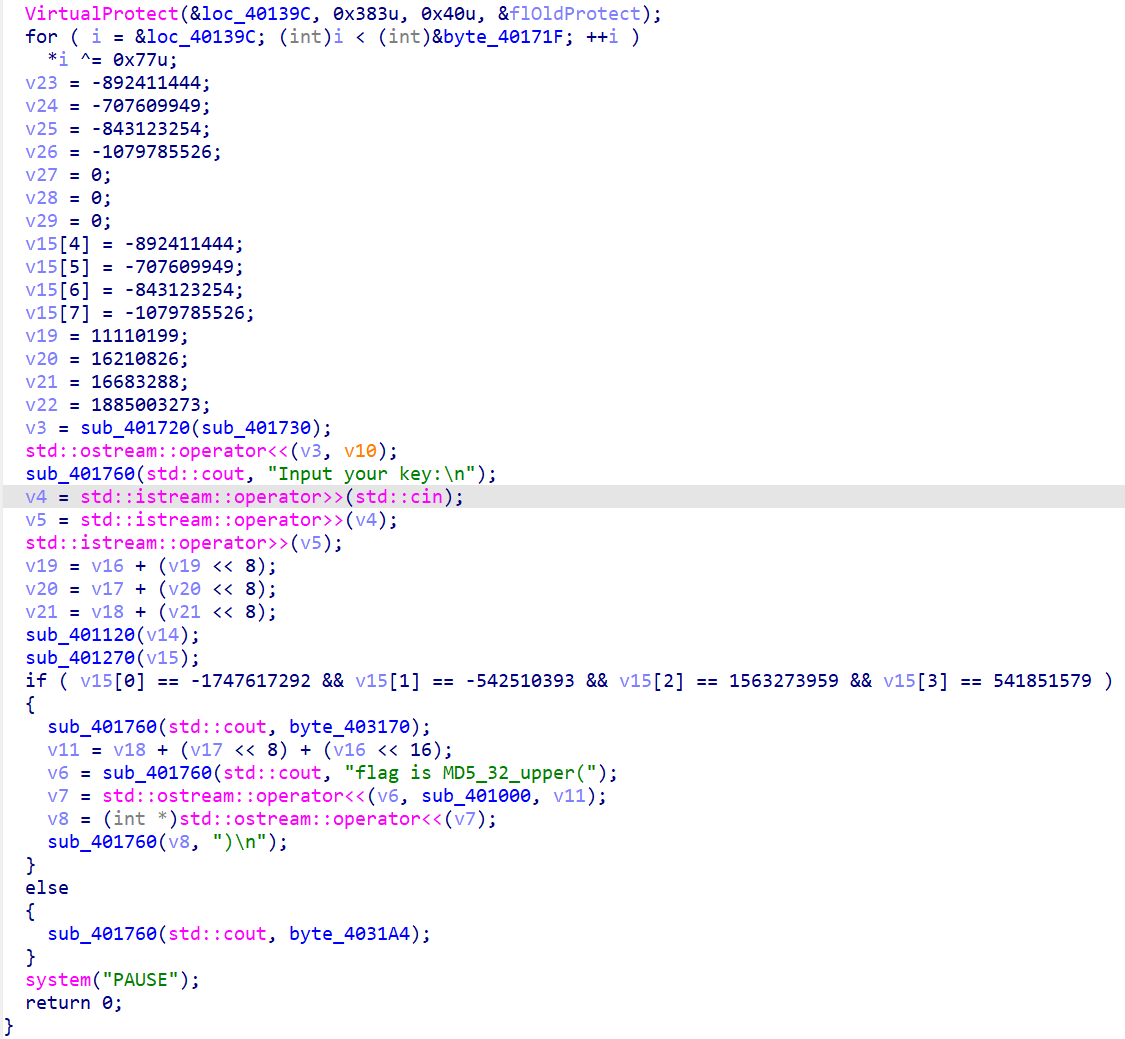
通过findcrypt插件可以知道程序使用的是SM4加密,我们的输入是秘钥的一部分。需要使得加密后的数据是v15。考虑爆破,写出如下代码:
1 |
|
4分钟之后可以解得正确秘钥:241 129 204。
得到flag:TSCTF-J{99B099BA10008E22180634253E984A88}
The_Native
本文采用JEB作为反汇编软件。
打开后可以在Manifest中找到程序的入口点是com.linjhs.ezandroid.MainActivity:
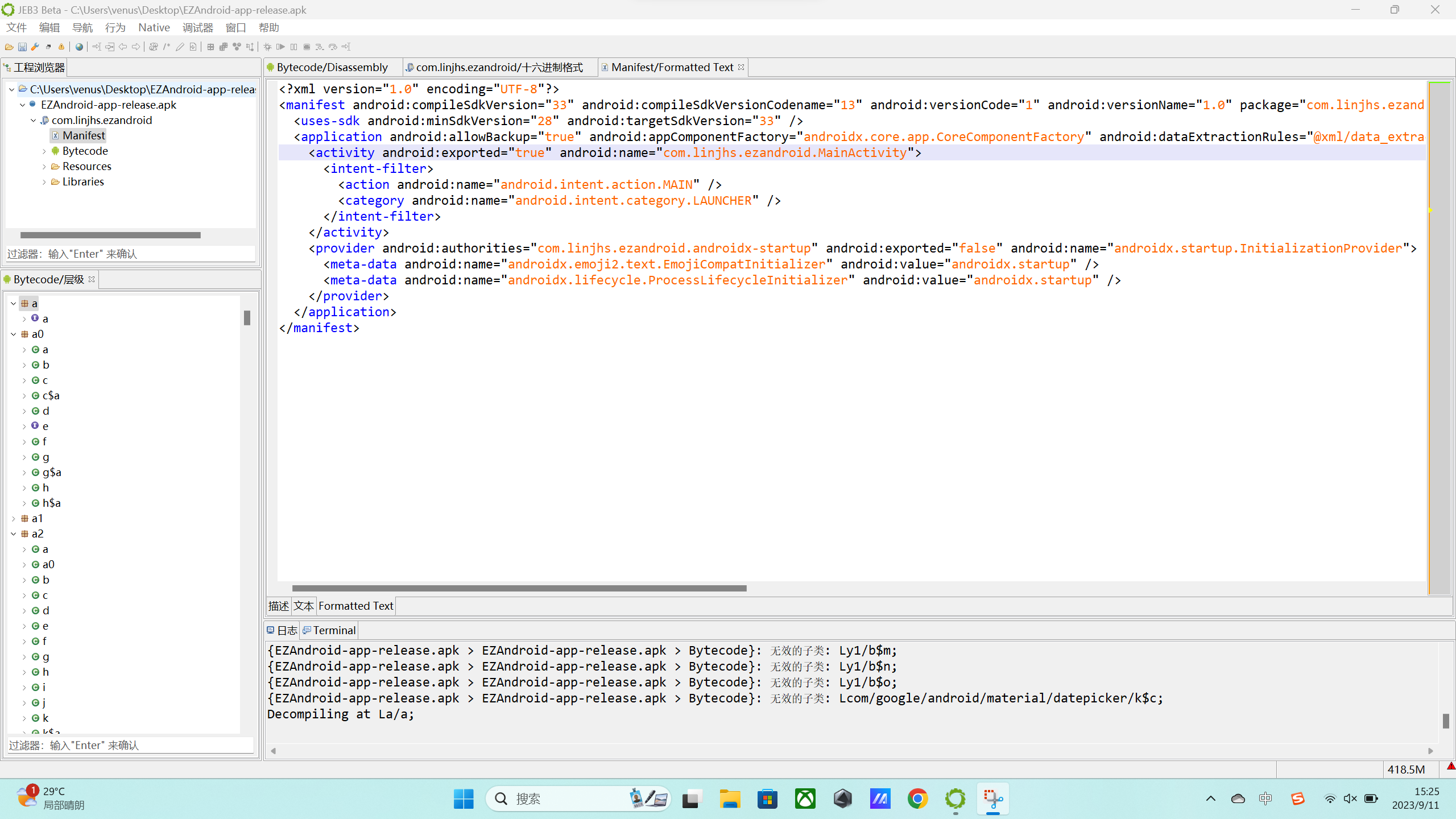
它调用了两个本地的库,一个叫MyString(),一个是Cal()。将libezandroid.so提取出来并用IDA打开后就可以找到他们。
对于MyString(),它只是将数据提取了出来然后返回。
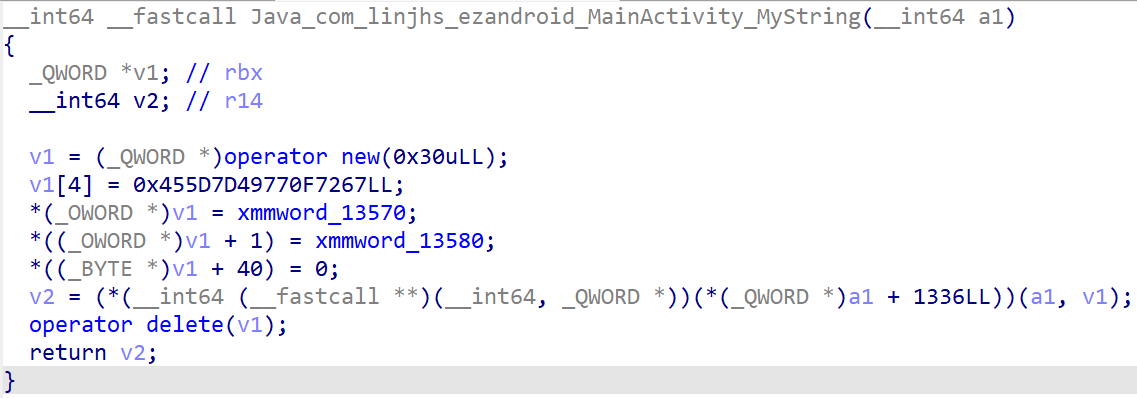
对于Cal(),有用的部分只有异或0xC。
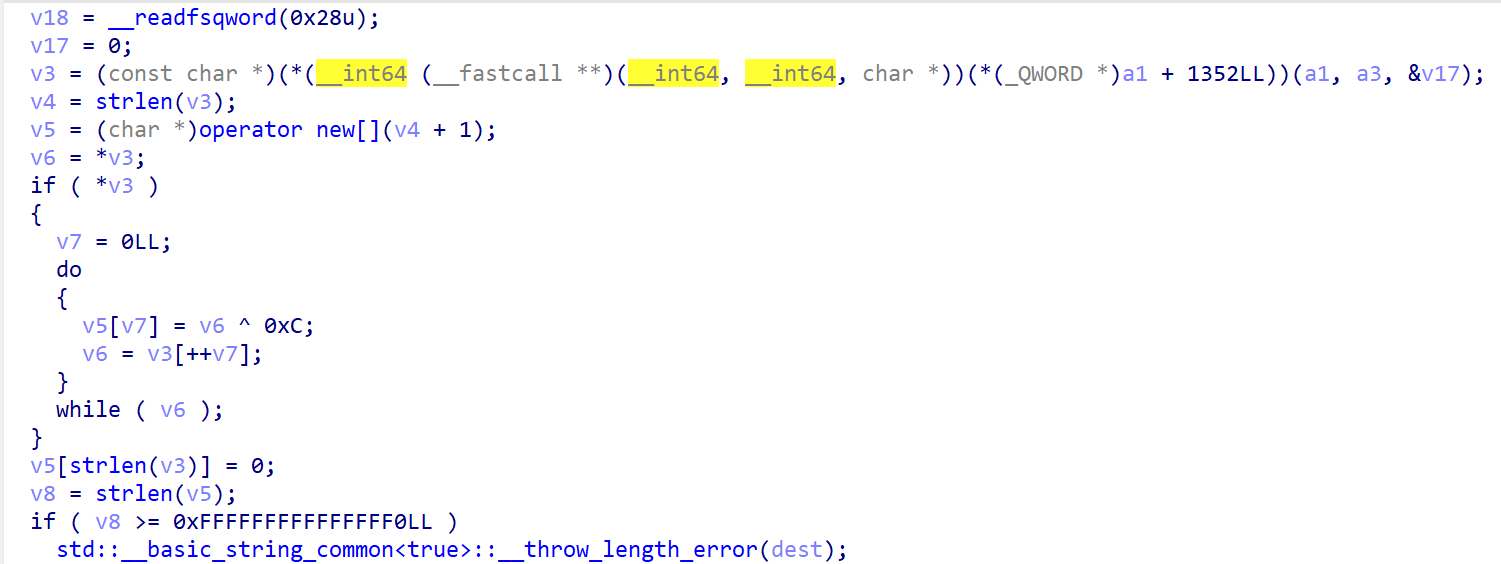
在MainActivity中可以找到异或52。因此可以写出解题代码:
1 |
|
运行得出flag:TSCTF-J{The_natiVe_alway5_h31p_y0u!}
The_Devil
虚拟机逆向。感受脑干在未知的地方被碾得支离破碎的感觉吧!哈哈哈哈哈哈哈!
经过分析可以得出:
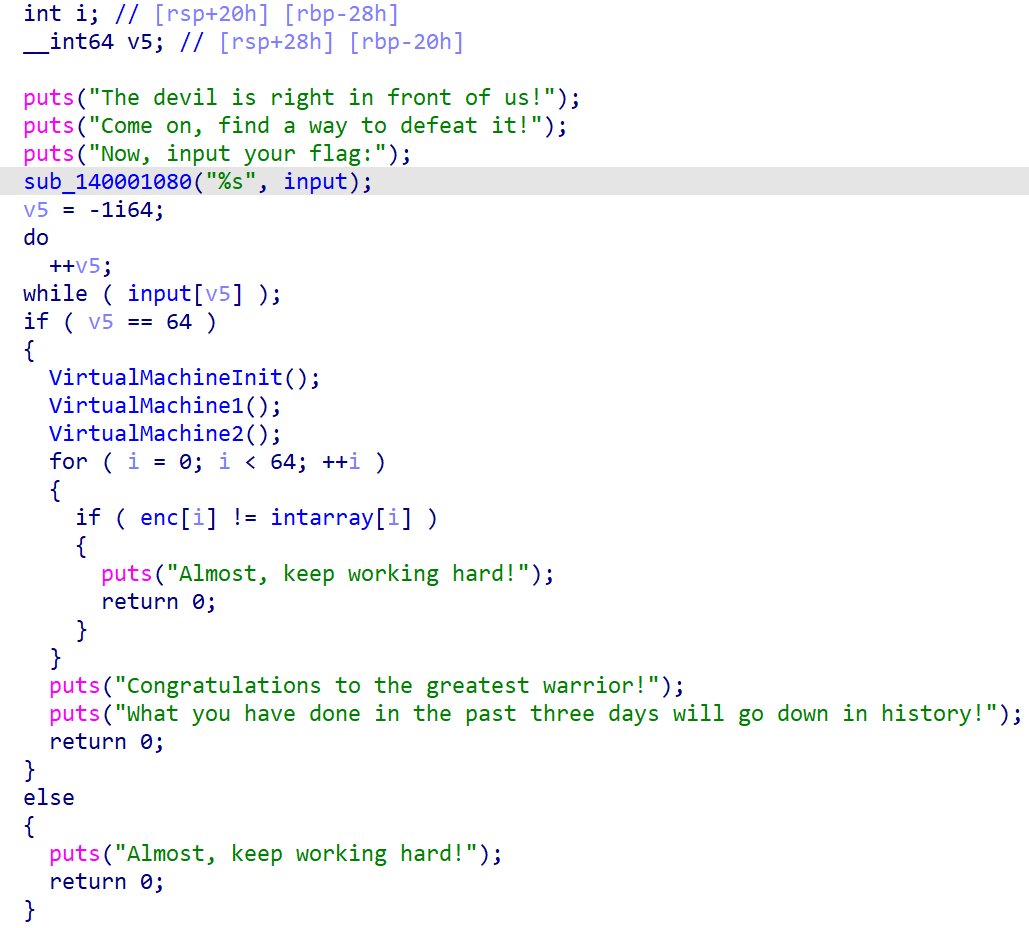
VirtualMachineInit()将寄存器及zf指示位置零。VirtualMachine1()分析后如下:
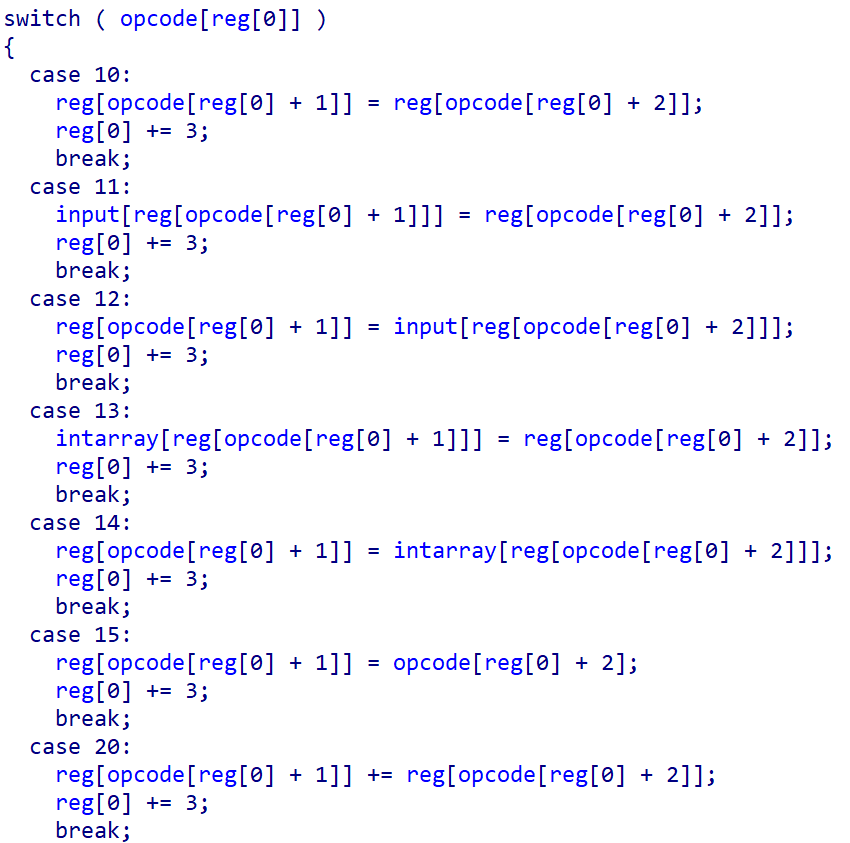
其中reg[0]是eip,reg[1]~reg[4]是eax,ebx,ecx,edx,reg[5]是zf指示位。
可以看出case1X是mov指令、case2X是add指令、case3X是sub指令、case4X是xor指令、case5X是imul指令、case6X是自创模运算modul指令、case7X是and指令、case8X是or指令、case90是not指令、case100是cmp指令、case110是jne指令、case111是je指令、case255是retn指令。再根据opcode可以复现出汇编代码:
1 | mov eax, 0 15,1,0, |
把上面的主要部分翻译成人话就是
1 | input[i] -= i; |
VirtualMachine2()可分析如下:
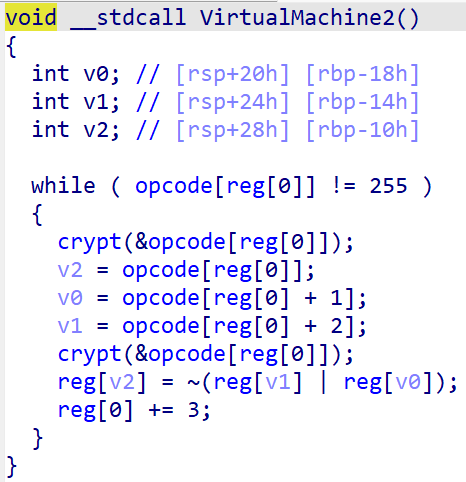
这一部分的加密由reg作为索引,进行或非操作。而此部分的opcode是加密过的,每次用完又会加密回去。加密所用的key明面上是"Clovershrub",动调可以发现实际上是"ClovershrubHMS"。可以考虑将所有的opcode自行解密,本文采用设置条件断点,让IDA输出的方法。
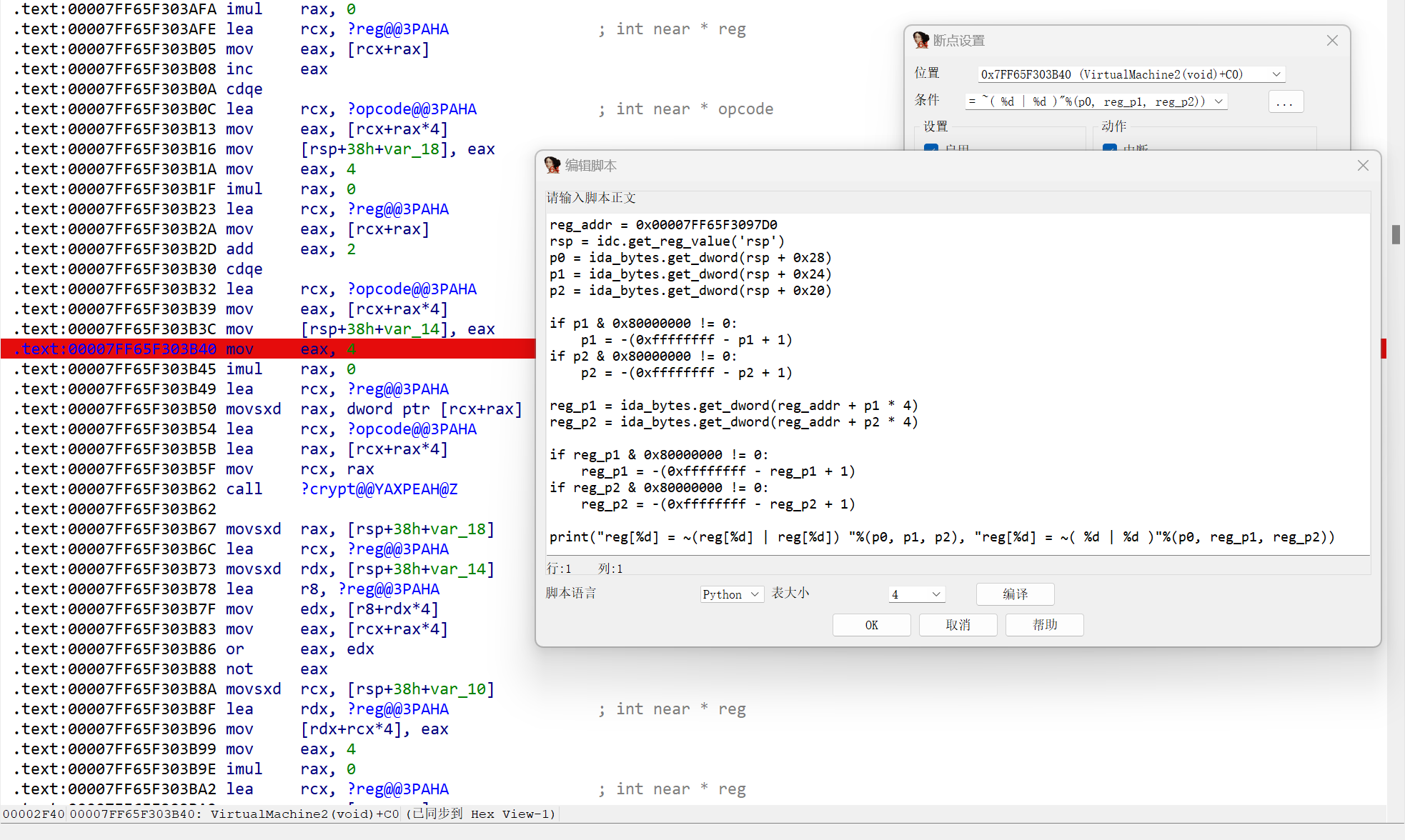
IDAPython脚本如下:
1 | reg_addr = 0x00007FF65F3097D0 |
在输出窗口可以看见他吐出来了一大堆东西。可对其进行分组,这是其中的第一个:
1 | reg[1] = ~(reg[8] | reg[8]) reg[1] = ~( 0 | 0 ) |
通过观察可以找到reg[8]就是intarray[0],reg[-432]是另一个数组——text[]的首位元素。进IDA查找可以知道text[]=“LoveCanConquerEverything”。分析或非操作可知其实就是在进行异或操作。我们可以写出解题代码:
1 |
|
运行得出flag:TSCTF-J{You_successfully_dispelled_the_devil_within_three_days!}
后记
这次经历还是收获了很多的。在赛前去各个网站扒往年的题学习它们的设计和解题的方法、赛中给选手回答问题都让我受益匪浅。要说遗憾的话可能是今年的题出得确实有点难,没见到几个成功屠龙的猛士。在看大家写得题解的时候发现有的师傅放弃一道题的原因竟然是害怕接下来还会有坑。哎,为什么要把我想象得如此邪恶。呜呜呜呜呜( ಥ _ ಥ )
不过你们应该还是挺喜欢我出的题的,对吧对吧?( ≧ ∇ ≦ ) /

![[TSCTF-J2024]二进制漏洞题解](/img/%5BTSCTF-J2024%5D%E4%BA%8C%E8%BF%9B%E5%88%B6%E6%BC%8F%E6%B4%9E%E9%A2%98%E8%A7%A3/cover.jpg)


